IBM X-Force has observed a renewed Banking malware Grandoreiro campaign that began in March 2024. This follows a law enforcement disruption of the operators in January. The threat actors behind Grandoreiro Banking Trojan appear to have reconstituted and are now targeting banks wordwide.
The ongoing campaign has targeted over 1,500 banks across more than 60 countries globally. Regions impacted include Central and South America, Africa, Europe, and the Indo-Pacific region. Grandoreiro infiltrates financial institutions to enable theft from customers’ accounts.
IBM’s analysis indicates the banking trojan is likely offered as a Malware-as-a-Service (MaaS). This business model allows criminal groups to develop and maintain the malicious code while renting access to other cybercriminals. With a wide geographic scope and hundreds of banks already targeted, the resurgent Grandoreiro campaign demonstrates the ongoing difficulty of fully dismantling organized cybercriminal operations.
Details of Banking Malware Grandoreiro Trojan
Grandoreiro Banking Trojan is a modular backdoor that supports:
- Command execution on the infected system
- Manipulating windows and navigation on the victim’s machine
- C2 Domain Generation via DGA (Domain Generation Algorithm)
- Auto-Updation for newer versions and modules of the malware
- Keylogging to steal passwords and credentials
- Imitating mouse and keyboard movements to automate tasks
- Guiding the victim’s browser to a certain URL for phishing
- Web-Injects to inject content into websites and restrict access to others
- Supporting modular extensions for additional functionality
Technical Analysis of Grandoreiro Banking Trojan
The latest version of Banking malware Grandoreiro shows significant upgrades to its string decryption abilities and domain generation algorithm (DGA). It can now leverage compromised Microsoft Outlook clients to spread further phishing emails.
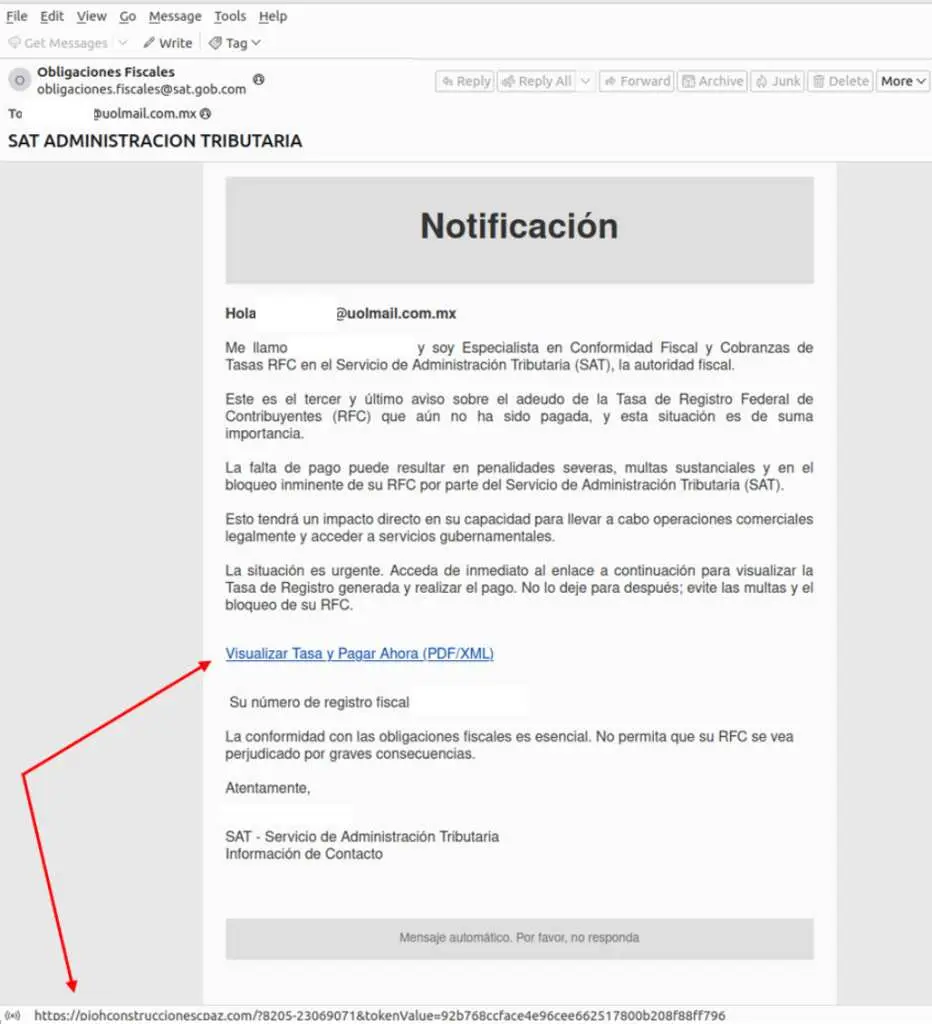
Historically focused on Latin America, Spain and Portugal, Grandoreiro’s operators have more recently targeted various agencies across Mexico and South Africa. Entities hacked include Mexico’s Tax Administration Service (SAT), Federal Electricity Commission (CFE) and Secretary of Administration and Finance. Argentina’s Revenue Service and South Africa’s SARS have also been impacted. This demonstrates the threat actors expanding Grandoreiro’s reach on a global scale, starting with attacks in South Africa.
In each incident, recipients were instructed to click a link for an invoice, fee statement or payment. Targeted users in Mexico, Chile, Spain, Costa Rica, Peru or Argentina were redirected to a fake PDF icon, while a ZIP file downloaded covertly in the background. These ZIPs contained a large executable disguised as a PDF, crafted on the day of or prior to the phishing email’s dissemination. The attacks aimed to sneak malicious payloads past security by mimicking legitimate files expected by recipients.
The Grandoreiro banking Trojan loader is artificially inflated to an exceptionally large size of over 100MB, allowing it to evade automatic antivirus scanning during execution. It further circumvents detection by displaying a small CAPTCHA popup imitating Adobe PDF reader, requiring users to click before continuing the installation process.
The loader also checks if it is running within a sandbox, verifying legitimate victims by enumerating basic system data sent back to the command and control server. Upon confirmation, it proceeds to download, decrypt and install the full Grandoreiro banking trojan payload.
Notably, the malware ceased running if the infected system had a public IP originating from Russia, Czechia, Poland or the Netherlands. It also blocked infections on outdated and unsupported Windows 7 machines in the United States without antivirus software installed.
Once active, the Grandoreiro banking trojan establishes persistence using Windows registry modifications. It then leverages an updated DGA to initiate outbound connections for receiving additional commands from command and control infrastructure awaiting further instruction. These evasive methods aided the threat actor’s illicit activities.
“One of Grandoreiro’s most interesting features is its capability to spread by harvesting data from Outlook and using the victim’s account to send out spam emails. There are at least 3 mechanisms implemented in Grandoreiro to harvest and exfiltrate email addresses, with each using a different DGA seed.”
“By using the local Outlook client for spamming, Grandoreiro can spread through infected victim inboxes via email, which likely contributes to the large amount of spam volume observed from Grandoreiro.” States the report.
To leverage compromised Microsoft Outlook clients for spreading further phishing emails, the Grandoreiro banking malware interacts with the local Outlook client by leveraging the Outlook Security Manager tool.
This allows it to prevent the Outlook Object Model Guard from triggering security alerts when it detects access to protected objects. Bypassing these security notifications within Outlook gives the Grandoreiro malware covert access needed to disseminate spam and phishing campaigns from hacked systems undetected. The use of legitimate security tools makes the intrusions more difficult to identify and remediate.
“The updates made to the malware, in addition to the significant increase in banking applications across several nations, indicate that the Grandoreiro distributors are seeking to conduct campaigns and deliver malware on a global scale.” States IBM Report









