State-Sponsored Hackers Exploit Webmail XSS Flaws in Global Cyberespionage Operation
A large-scale cyberespionage campaign known as RoundPress has targeted high-level government, military, and infrastructure entities across multiple countries using XSS vulnerabilities in popular webmail platforms.
The operation, active since 2023 and continuing through 2024, has been linked to Russian threat group APT28—also known as Fancy Bear or Sednit—with medium confidence by ESET researchers.
RoundPress weaponized both zero-day and n-day cross-site scripting (XSS) vulnerabilities to steal sensitive data from government webmail systems.
Targets Include Governments, Military Units, and Defense Firms
The campaign’s victims include:
- Government agencies in Greece, Ukraine, Serbia, and Cameroon
- Military units in Ukraine and Ecuador
- Defense contractors in Ukraine, Bulgaria, and Romania
- Critical infrastructure entities in Ukraine and Bulgaria

RoundPress targets
Source: ESET
No-Click Email Exploit Using Embedded JavaScript
The attack chain begins with a spear-phishing email crafted to resemble real political or news content. Once a target opens the message in a webmail browser, a malicious JavaScript payload embedded in the email’s HTML body automatically executes—without requiring any clicks or input from the user.
The script then:
- Tricks the browser or password manager into autofilling login credentials
- Scrapes email content, contacts, and account settings
- Collects login history and two-factor authentication details
- Sends all collected data to attacker-controlled servers using HTTP POST requests
The payload executes only when the email is opened and does not persist beyond that session. The scripts are customized per webmail platform.
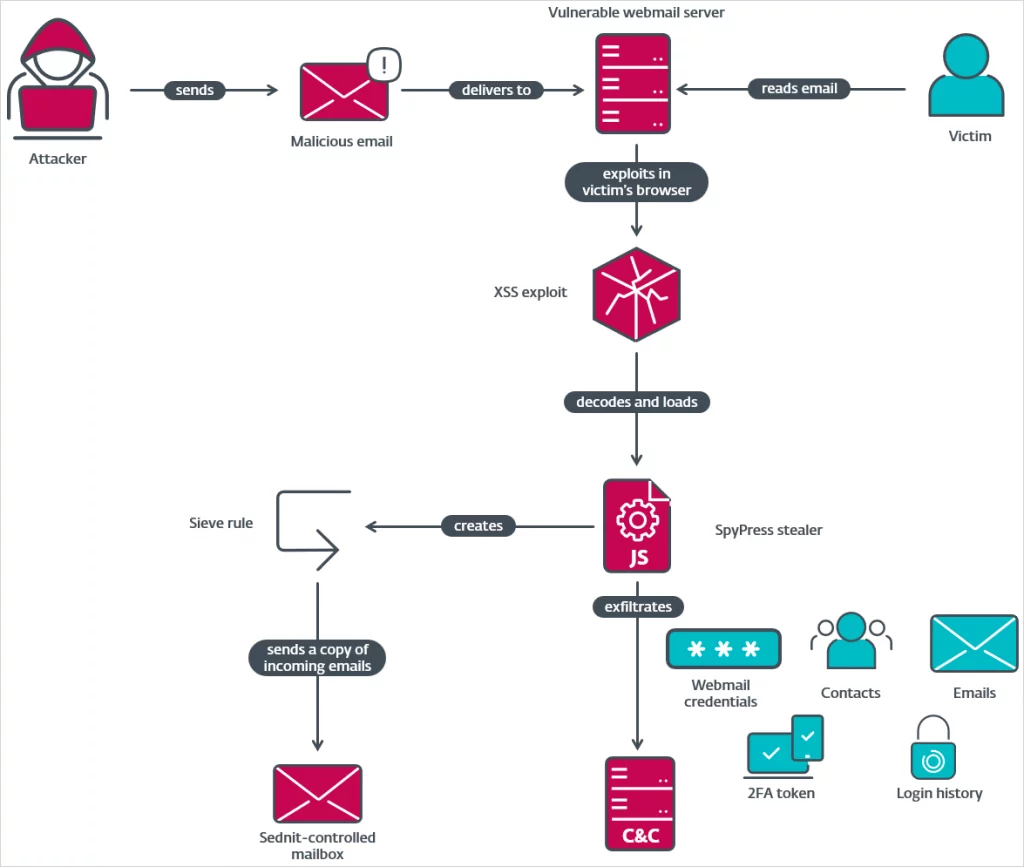
Attack chain overview
Source: ESET
Webmail Platforms and Vulnerabilities Exploited
ESET identified multiple XSS flaws exploited by APT28 in various enterprise-grade webmail products:
- Roundcube – CVE-2020-35730
Stored XSS via embedded JavaScript in email body. Triggered on open, used for data and credential theft (2023). - Roundcube – CVE-2023-43770
XSS in hyperlink handling. Attackers injected<script>tags via improperly sanitized email content (early 2024). - MDaemon – CVE-2024-11182
Zero-day in HTML parser. Exploited via malformed<noembed>with hidden<img onerror>payload, enabling 2FA bypass and App Password abuse (late 2024). - Horde – Unconfirmed XSS
Attempted exploitation using<img onerror>scripts. Likely blocked by modern security filters; vulnerability remains unidentified but appears patched. - Zimbra – CVE-2024-27443
First known use of XSS in calendar invite parsing. Attackers injected base64-encoded scripts via unsanitizedX-Zimbra-Calendar-Intended-Forheader.
Campaign Still a Threat in 2025
Although ESET has not observed new RoundPress activity in 2025, the techniques used—especially no-click XSS exploits—remain viable due to the steady emergence of new vulnerabilities in widely-used enterprise webmail platforms.
“All that is needed from the victim is to open the email… the malicious JavaScript script executes,” ESET researchers explained.
Organizations are urged to patch email systems promptly and monitor for suspicious webmail activity to reduce exposure to similar attacks.









