A critical unauthenticated file upload vulnerability in SAP NetWeaver is under active exploitation, placing more than 1,200 exposed servers—including those of Fortune 500 firms—at serious risk of compromise.
CVE-2025-31324 Enables Full System Takeover
The flaw, tracked as CVE-2025-31324, affects the Metadata Uploader component of SAP NetWeaver Visual Composer. It allows remote attackers to upload arbitrary executable files without authentication, enabling code execution and full system compromise.
SAP disclosed the issue last week and released a workaround on April 8, 2025, followed by a patch on April 25. While SAP claims there is no evidence yet of customer data exposure, security firms say exploitation is well underway.
More Than 1,200 Vulnerable Servers Exposed Online
The Shadowserver Foundation initially identified 427 internet-exposed vulnerable servers, warning of the large attack surface. However, cybersecurity firm Onyphe reported a higher number—1,284 vulnerable servers, with 474 already compromised using malicious web shells such as cache.jsp, helper.jsp, or randomly named variants to evade detection.
According to Onyphe CTO Patrice Auffret, approximately 20 Global 500 companies are either vulnerable or already compromised.
Global Exposure Across Major Economies
The geographic breakdown of exposed systems highlights a global risk:
- United States – 149
- India – 50
- Australia – 37
- China – 31
- Germany – 30
- Netherlands – 13
- Brazil – 10
- France – 10
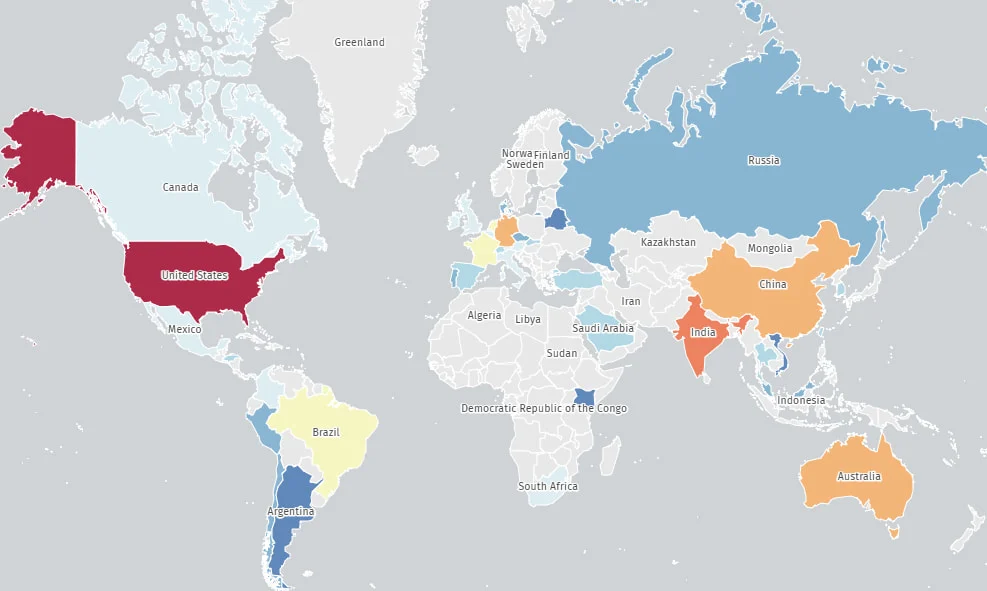
Location of vulnerable SAP NetWeaver instances
Source: The Shadowserver Foundation
Given SAP NetWeaver’s widespread use in large enterprise environments, even a relatively small number of compromised instances presents significant downstream risk.
Mitigation and Detection Guidance
SAP urges all customers to apply the latest patch immediately. If patching is not feasible, the following mitigations are advised:
- Restrict access to
/developmentserver/metadatauploader - Disable Visual Composer if not in use
- Forward logs to a SIEM and scan servlet paths for unauthorized files
In addition, RedRays has released a scanner for CVE-2025-31324 to assist in identifying vulnerable instances across large environments.
SAP has acknowledged awareness of the exploitation attempts and may provide further updates. Meanwhile, threat activity is expected to continue escalating.