A new phishing campaign is targeting WooCommerce administrators with fake security alerts designed to hijack websites by installing hidden backdoors and persistent malware.
Phishing Campaign Disguised as Security Update
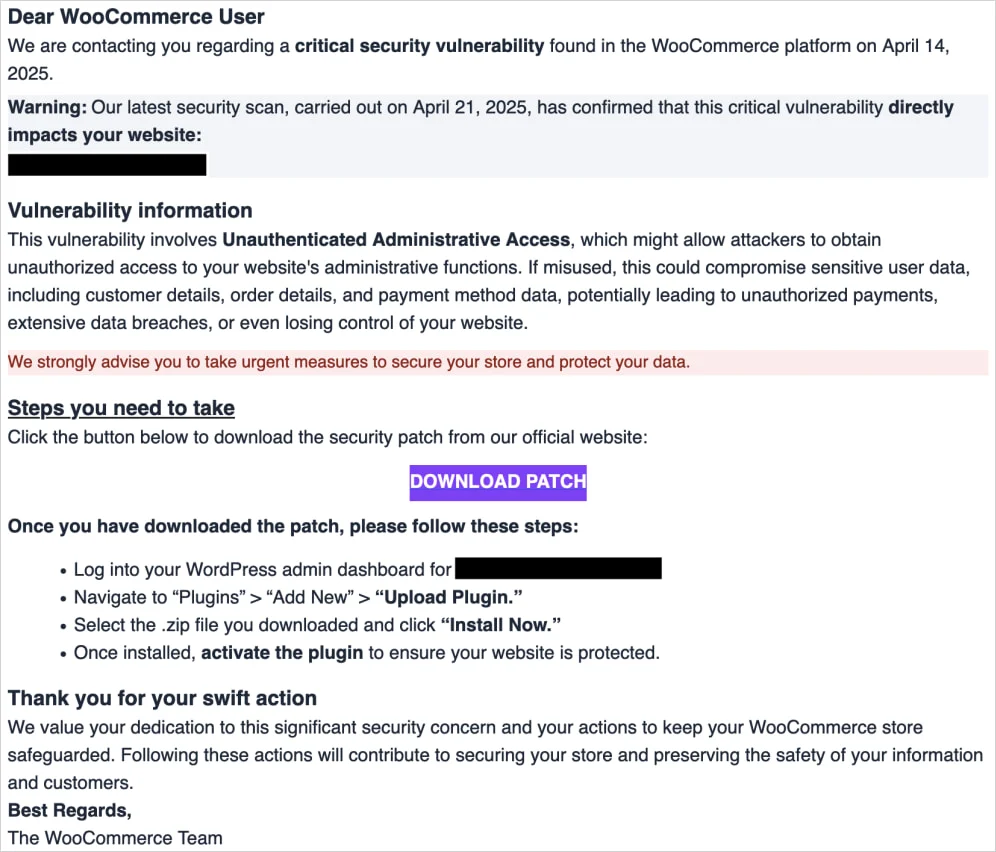
The attack starts with phishing emails that impersonate WooCommerce, sent from the spoofed address ‘help@security-woocommerce[.]com.’
Victims are warned about a supposed “unauthenticated administrative access” vulnerability and are urged to urgently download a critical patch.
Phishing email targeting WooCommerce users
Source: Patchstack
The emails reference fake scan dates, including April 14 and April 21, 2025, to create urgency.
Clicking the embedded “Download Patch” button directs users to a fake WooCommerce website at ‘woocommėrce[.]com,’ where a subtle homograph attack replaces the letter “e” with the Lithuanian character “ė.”
Malicious Plugin Installs Hidden Admin Accounts and Web Shells
The downloaded file (“authbypass-update-31297-id.zip”) installs a malicious plugin that immediately creates a cronjob, running every minute, to generate a hidden admin-level user.
It then connects to ‘woocommerce-services[.]com/wpapi’ to retrieve a second-stage obfuscated payload.
Multiple PHP-based web shells, including P.A.S.-Form, p0wny, and WSO, are deployed under ‘wp-content/uploads/,’ providing full control over the infected site.
Risks for Infected WooCommerce Sites
The attackers can use the web shells to:
- Inject ads
- Steal payment card information
- Redirect site visitors to malicious pages
- Enlist the server in DDoS botnets
- Deploy ransomware to encrypt site data
To avoid detection, the plugin hides itself from the WordPress admin panel and conceals the newly created admin account.
Signs of Compromise and Recommended Actions
Patchstack advises WooCommerce site owners to check for:
- Unknown 8-character admin accounts
- Unusual cronjobs running at high frequency
- A folder named ‘authbypass-update’
- Outgoing requests to domains like ‘woocommerce-services[.]com,’ ‘woocommerce-api[.]com,’ or ‘woocommerce-help[.]com’
Security experts warn that threat actors frequently rotate these indicators once discovered, so broader scans and security reviews are advised.
More technical details are available in Patchstack’s official advisory and security community updates.









