Attackers are leveraging Google’s own infrastructure—specifically OAuth applications and DKIM-signed alerts—to conduct phishing attacks that appear completely legitimate. A recent incident involving a spoofed subpoena email highlights how threat actors are exploiting gaps in Google’s security design to trick even technically aware users.
Security Researcher Identifies Google-Signed Phishing Attempt
Nick Johnson, lead developer of the Ethereum Name Service (ENS), received what appeared to be a legitimate security alert from Google. The message informed him of a subpoena requesting access to his account content.
At first glance, everything looked authentic. The message even appeared in the same email thread as other genuine Google alerts. But Johnson noticed the support portal link led to sites.google.com instead of the official accounts.google.com.
“The only hint it’s a phish is that it’s hosted on sites.google.com,” Johnson noted, calling the portal an “exact duplicate of the real thing.”
DKIM Replay Attack Makes Email Appear Authentic
The phishing email was more than just well-crafted—it passed Google’s DKIM verification, making it appear entirely genuine in the inbox.
Johnson discovered that the attacker had used a method known as a DKIM replay attack, where a legitimate Google-signed alert is repurposed and forwarded to a target.
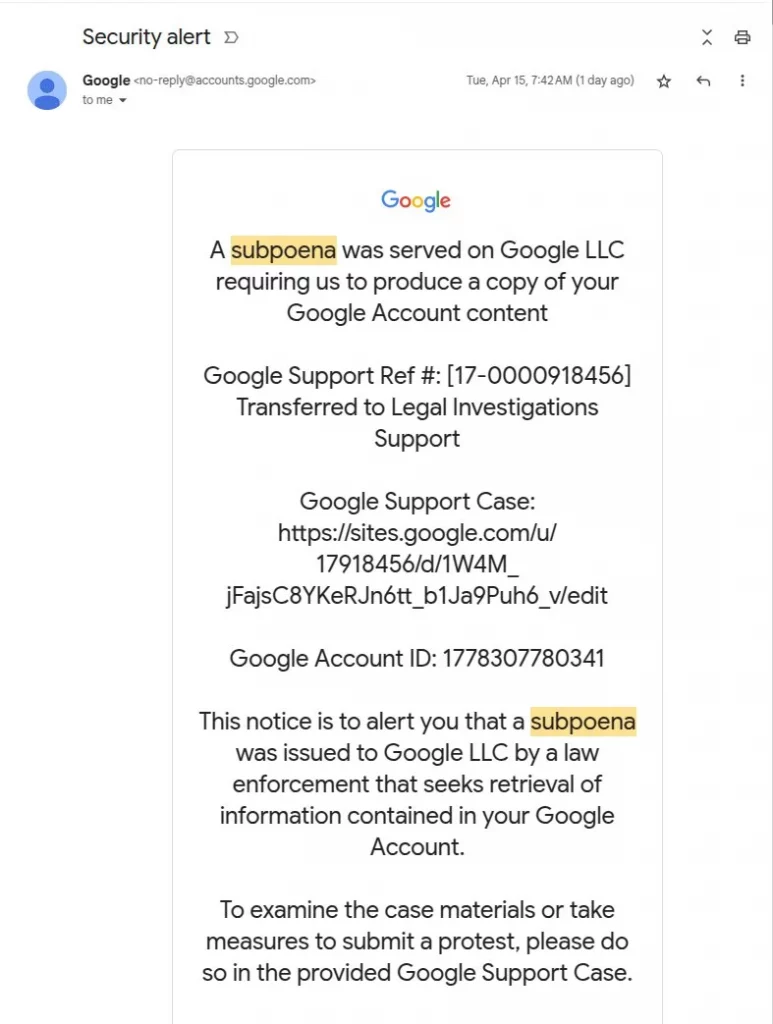
Phishing email relayed through Google systems
source: Nick Johnson
How the attack worked:
- The attacker registered a domain and created a Google account with an address like
me@domain. - They then created an OAuth application with a name that contained the phishing message, separated from Google’s security notification with excess whitespace.
- When the attacker gave the app access to their account, Google sent a security alert confirming the access.
- Because the message was auto-generated by Google, it was signed with a valid DKIM key.
- The attacker then forwarded the DKIM-signed message to victims, making it appear legitimate.
Due to how DKIM works, it only verifies the headers and message body—not the envelope. This allows attackers to repurpose legitimate messages without invalidating the DKIM signature.
Other Platforms Targeted: PayPal Case Mirrors Google Exploit
A similar attack was observed in March targeting PayPal users. In that case, the attacker used the “gift address” feature to add an email and pasted the phishing content into a second form field.
PayPal then sent a confirmation to the attacker’s email, which was forwarded to a mailing list and distributed to all intended victims.
The email, being system-generated by PayPal, also passed DKIM checks, making it appear trustworthy.
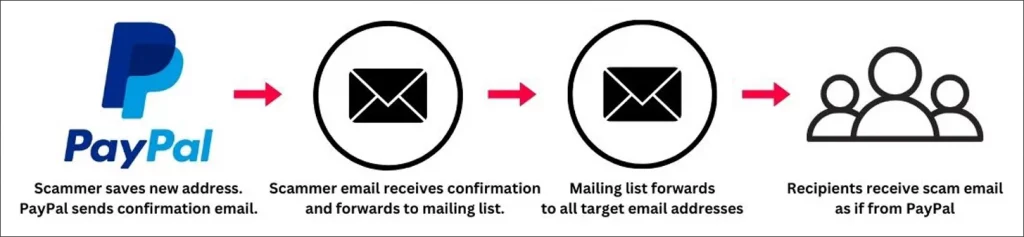
PayPal scam uses similar trick
source: BleepingComputer
Google Acknowledges Risk and Prepares a Fix
Initially, when Johnson submitted a bug report to Google, the company responded that “the process was working as intended.”
However, after reviewing the incident, Google acknowledged the risk and has since confirmed that a fix is in development to address the OAuth-related vulnerability.
Email security firm EasyDMARC has also published a detailed breakdown of the DKIM replay phishing technique, confirming the steps used by the attacker and reinforcing the need for more robust checks at the infrastructure level.










