South Korean conglomerate SK Group joins growing list of Qilin ransomware targets in 2025
South Korea’s SK Group, a major player in energy, semiconductors, and telecommunications, has been claimed as the latest victim of the Qilin ransomware gang, which alleges to have stolen 1 terabyte of sensitive files in its most recent cyberattack.
The gang posted a new update to its dark web blog on Friday, featuring an image that appears to show a video conference between SK executives and a U.S. official, with an American flag visible in the background.
One commenter on the post wrote,
“Is the U.S. investing? Interesting, of course. Now there will be many people willing to buy such information.”
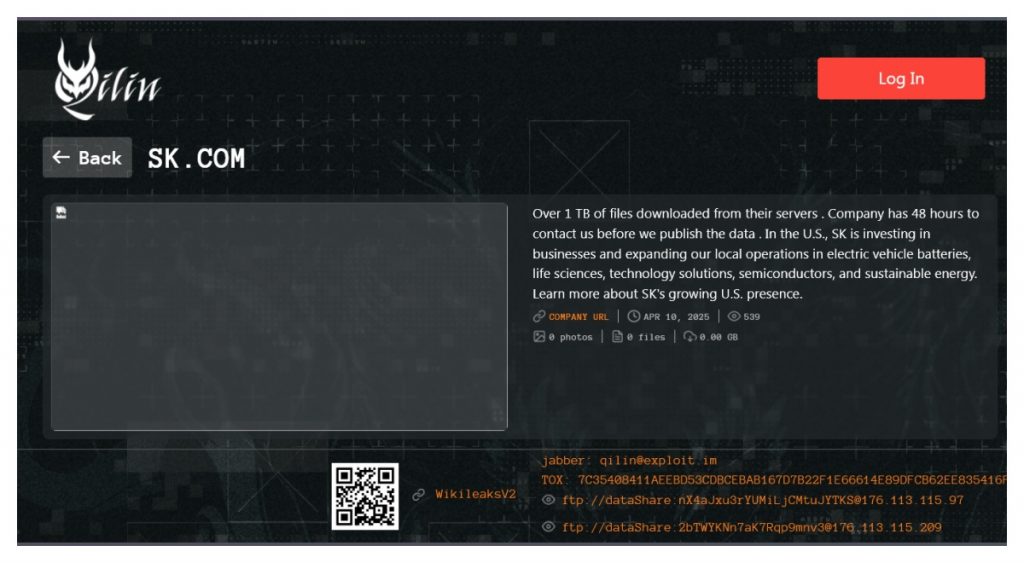
Qilin leak site
SK Group: Global Reach and Economic Impact
SK Group is one of South Korea’s largest business conglomerates, second only to Samsung. Headquartered in Seoul, SK operates over 260 affiliate companies worldwide and employs more than 80,000 people globally. The conglomerate spans industries including:
- Information and Communications Technology (ICT)
- Advanced materials
- Biopharmaceuticals
- Mobility and EV batteries
- Life sciences
- Energy and telecommunications
SK had 2024 revenues of $91.15 billion, according to Companies Market Cap, and currently lists 16 companies on the Korea Exchange.
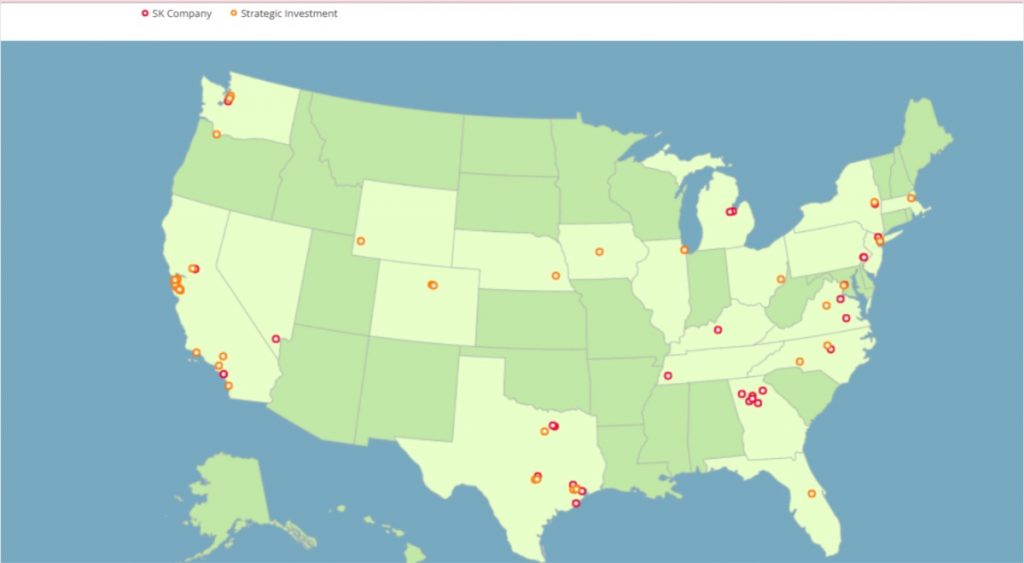
Image by SK Group
The group’s U.S. investments exceed $50 billion, spread across 20 states, positioning it as a significant foreign investor and an appealing target for ransomware operations.
Qilin Gang Expands Reach With Aggressive 2025 Campaign
Qilin, also known as “Agenda,” operates a ransomware-as-a-service (RaaS) model and is known for using double extortion tactics—demanding ransom for file decryption and a second payment to prevent public leaks.
The group is reportedly of Russian origin, avoiding targets in CIS (Commonwealth of Independent States) countries. Qilin gained notoriety in June 2024 for a $50 million ransomware attack on the UK’s NHS partner Synnovis Labs, which led to the disruption of medical services across five London hospitals.
In February 2025, Qilin claimed attacks on:
- Lee Enterprises, a major U.S. newspaper publisher
- Utsunomiya Cancer Center in Japan, exposing data of 300,000 patients
- Detroit’s PBS affiliate and the Houston Symphony
The attack on the Utsunomiya center rendered the hospital’s systems “unusable.”
256 Known Victims to Date
According to Cybernews’ Ransomlooker tool, Qilin has claimed 256 victims over the past year, up from 191 in early March—reflecting a one-third increase. In the last four weeks alone, Qilin has added 68 new victims, placing it second in activity behind Babuk, another rising ransomware group.
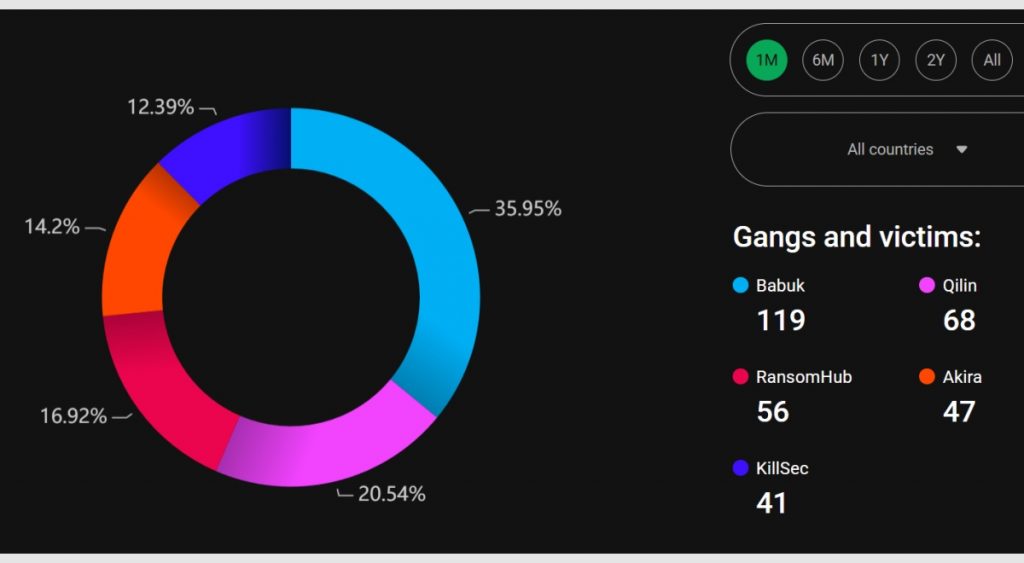
Cybernews Ransomlooker
Advanced Tactics and Custom Ransomware
Qilin’s latest strain, Qilin.B, is written in the Rust programming language, offering custom encryption options for its affiliates. As outlined in a January 2025 Blackpoint report, Qilin now uses:
- Harvested Google Chrome credentials
- Techniques to evade Endpoint Detection and Response (EDR) tools
- Exploitation of the “Citrix Bleed” zero-day vulnerability
The Citrix bug, patched in late 2023, remains a common entry point due to delays in patch implementation by targeted firms. This same exploit was used by ALPHV/BlackCat in the United Health cyberattack.
Previous Victims and Industry Focus
Qilin frequently targets critical sectors such as healthcare and manufacturing. Past victims include:
- Yanfeng, a top auto parts supplier for GM, Chrysler, Jeep, Dodge, and Ram
Despite the growing number of victims, SK Group has not publicly confirmed the breach or issued any official statement at the time of writing.









