A significant GitHub supply chain attack, targeting Coinbase in March 2025, has been linked to a compromised SpotBugs token. This attack highlights critical vulnerabilities within the open-source ecosystem and GitHub Actions.
This was discovered by Palo Alto Networks’ Unit 42 researchers who added an update yesterday on their original analysis of the incident.
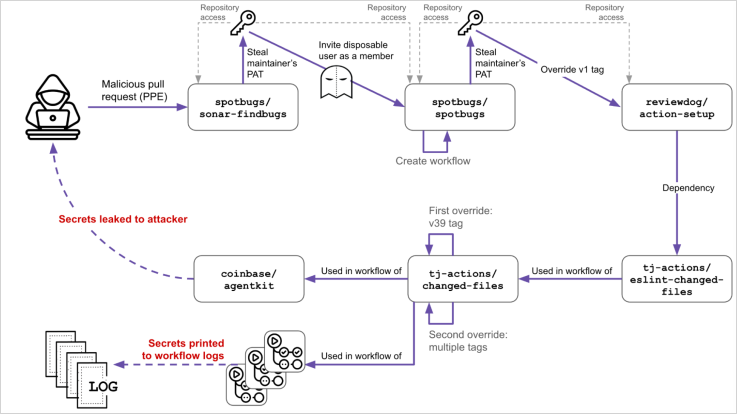
The attack unfolded over several months, beginning in November 2024 with the theft of a SpotBugs maintainer’s Personal Access Token (PAT). This PAT was inadvertently included in a CI workflow.
On December 6th, 2024, a malicious pull request from a throwaway account (“randolzflow”) exploited a vulnerable “pull_request_target” workflow, successfully stealing the maintainer’s PAT.
This stolen PAT was then used on March 11th, 2025, to add a malicious user (“jurkaofavak”) to the SpotBugs project. This malicious user pushed a compromised GitHub Actions workflow, exfiltrating a Reviewdog maintainer’s PAT (RD_MNTNR), who also had SpotBugs access.
This second stolen PAT granted write access to “reviewdog/action-setup,” enabling the attacker to replace the v1 tag with malicious code from a forked repository. This poisoned all users of v1.
The tainted v1 tag was subsequently used by “tj-actions/eslint-changed-files,” creating a backdoor that dumped secrets from CI runners into logs. While initially feared to affect 23,000 repositories, the attack ultimately exposed secrets in 218 repositories.
The attackers specifically targeted “coinbase/agentkit,” attempting to breach Coinbase’s infrastructure on March 14th, 2025. However, Coinbase detected the breach and swiftly removed the compromised workflow, preventing any data exposure.
Supply chain attack diagram
Source: Unit 42
This meticulously planned attack underscores the fragility of trust within open-source projects and the need for enhanced security measures within the GitHub Actions ecosystem. The incident highlights the critical need to improve tag immutability and audit logging within GitHub Actions.
Key vulnerabilities exploited:
- Inclusion of PATs in CI workflows.
- Vulnerable “pull_request_target” workflows.
- Mutable git tags.
- Insufficient audit logging in GitHub Actions.
Recommendations for mitigation:
- Immediately rotate all secrets in affected projects.
- Audit GitHub Actions logs (March 10-14, 2025) for suspicious activity, particularly base64-encoded blobs.
- Pin dependencies using commit hashes instead of tags.
- Avoid using “pull_request_target” workflows unless absolutely necessary.
This GitHub supply chain attack serves as a stark reminder of the importance of robust security practices within the open-source development community. Enterprise businesses must prioritize secure coding practices, regular security audits, and proactive threat detection to mitigate the risk of similar attacks.










