A massive phishing campaign targeting nearly 12,000 GitHub repositories is exploiting fake “Security Alert” issues to compromise developer accounts. This sophisticated attack leverages a malicious OAuth application to gain complete control over users’ accounts and code.
The deceptive GitHub issues display a warning message stating:
“Security Alert: Unusual Access Attempt We have detected a login attempt on your GitHub account that appears to be from a new location or device.”
The message falsely claims unusual activity originating from Reykjavik, Iceland, and the IP address 53.253.117.8.
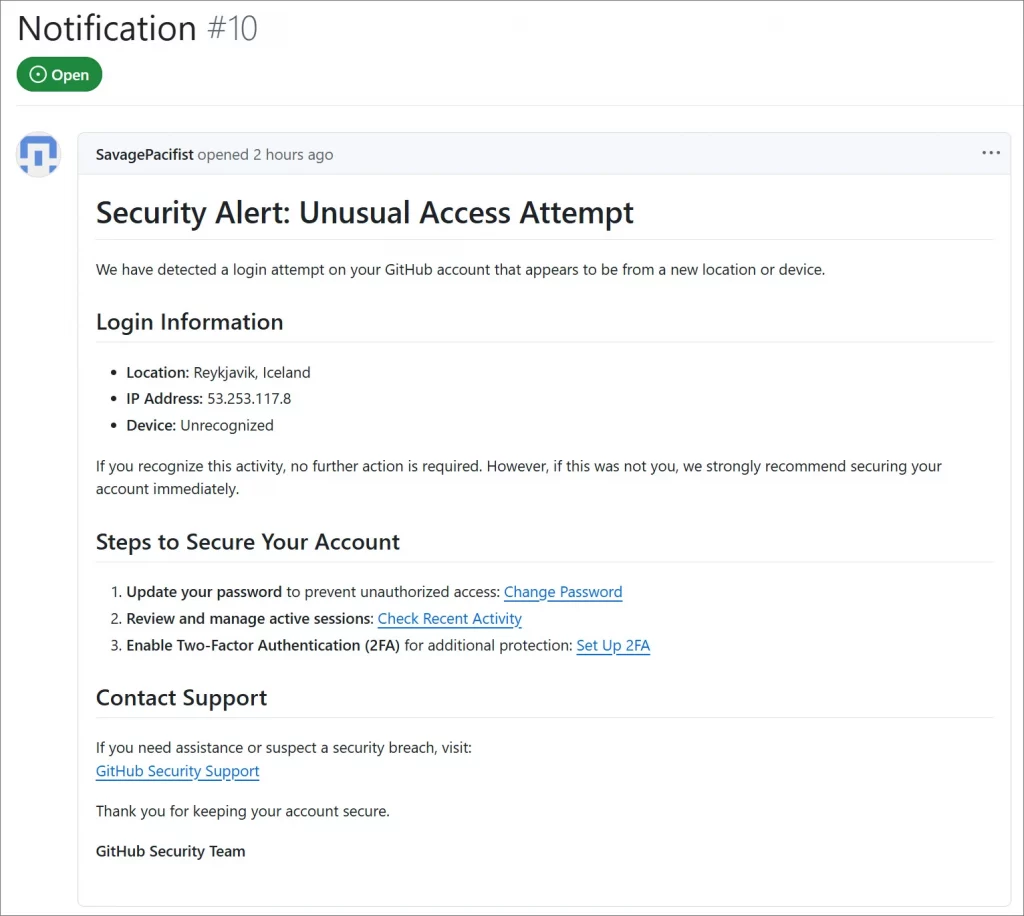
Fake “Security Alert” issue posted to GitHub repositories
Source: BleepingComputer
This consistent messaging across all affected repositories aims to create a sense of urgency and panic, prompting developers to take immediate action.
The fraudulent alert directs users to update their passwords, review active sessions, and enable two-factor authentication. However, these links lead to a GitHub authorization page for a malicious OAuth app named “gitsecurityapp.”
This “gitsecurityapp” requests extensive and dangerous permissions, granting attackers complete access to a user’s account and repositories. These permissions include:
Upon authorization, an access token is generated and sent to various web pages hosted on onrender.com, granting the attacker full control.
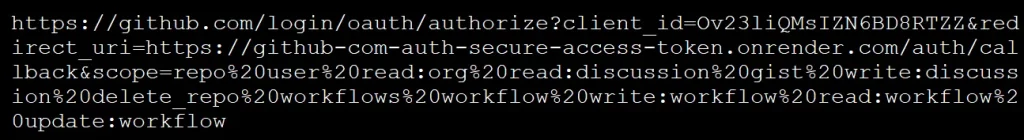
OAuth authorization link with a callback to an onrender.com page
Source: BleepingComputer
The attack, which began on March 16th, 2025, at 6:52 AM ET, is ongoing. While the number of targeted repositories fluctuates, indicating GitHub’s response, the scale of the attack remains significant.
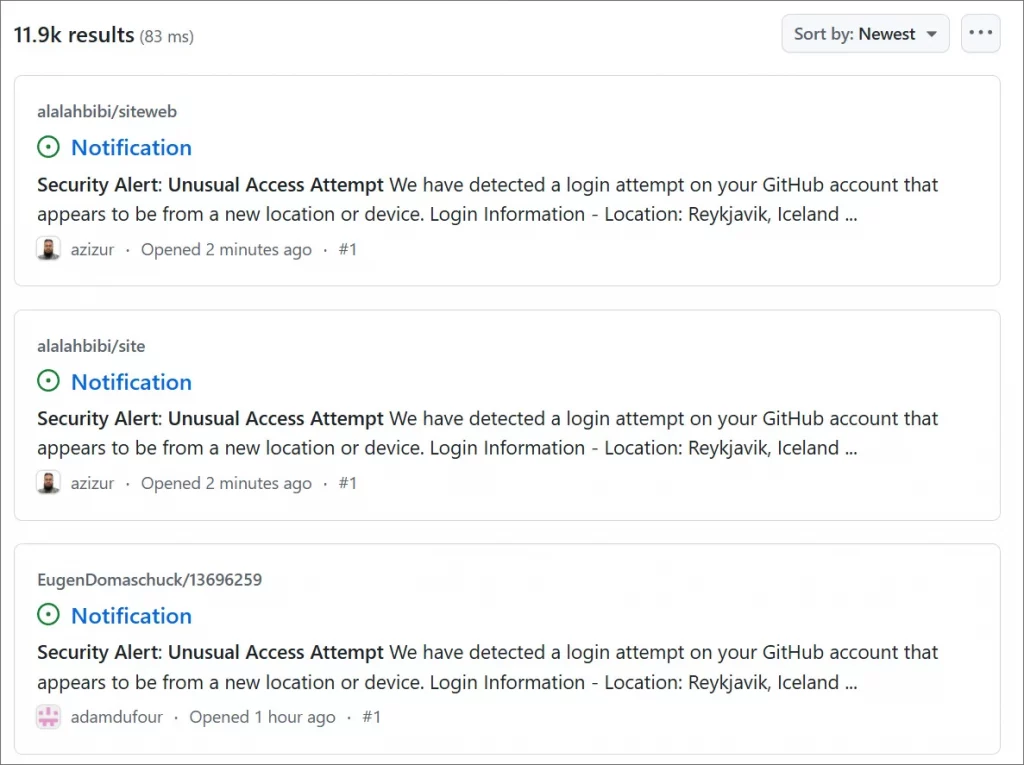
Fake security alert issues created in GitHub repositories
Source: BleepingComputer
If you’ve authorized the malicious “gitsecurityapp” OAuth app, immediately revoke its access through your GitHub Settings under “Applications.” Remove any unfamiliar or suspicious apps, particularly those with names similar to “gitsecurityapp.”
Check for new or unexpected GitHub Actions (Workflows) and the creation of private gists. Finally, change your passwords and rotate your authorization tokens. This is crucial to mitigate the impact of this OAuth attack.
Learn more about protecting yourself from Phishing Attacks on the Rise: Businesses Face Growing Cyberthreat.
Helpful Reads:









