Ransomware gangs are leveraging a critical vulnerability in Paragon Partition Manager to launch sophisticated Bring Your Own Vulnerable Driver (BYOVD) attacks. Microsoft identified five flaws in the BioNTdrv.sys driver, one of which (CVE-2025-0289) is actively being exploited as a zero-day.
Understanding the BYOVD Attack Vector
BYOVD attacks involve threat actors introducing a vulnerable kernel driver onto a target system. This driver, in this case, a compromised version of Paragon Partition Manager’s BioNTdrv.sys, allows privilege escalation.
“An attacker with local access to a device can exploit these vulnerabilities to escalate privileges or cause a denial-of-service (DoS) scenario,” warns a CERT/CC bulletin.
The use of a Microsoft-signed driver makes this attack particularly insidious, bypassing standard security measures.
Because BioNTdrv.sys operates at the kernel level, successful exploitation grants attackers SYSTEM-level privileges. This allows them to execute arbitrary code, bypassing security software and defenses.
Microsoft researchers discovered the flaws, noting that CVE-2025-0289 is being used by ransomware groups for privilege escalation. While the specific ransomware gangs involved remain undisclosed, the threat is significant.
Technical Details of the Paragon Partition Manager Vulnerabilities
The five vulnerabilities in Paragon Partition Manager are:
- CVE-2025-0288: Arbitrary kernel memory write due to improper handling of the ‘memmove’ function.
- CVE-2025-0287: Null pointer dereference from missing validation of a ‘MasterLrp’ structure.
- CVE-2025-0286: Arbitrary kernel memory write from improper validation of user-supplied data lengths.
- CVE-2025-0285: Arbitrary kernel memory mapping due to failure to validate user-supplied data.
- CVE-2025-0289: Insecure kernel resource access due to lack of validation of the ‘MappedSystemVa’ pointer.
The first four affect Paragon Partition Manager versions 7.9.1 and earlier. CVE-2025-0289, the actively exploited flaw, impacts version 17 and older.
“Microsoft has observed threat actors (TAs) exploiting this weakness in BYOVD ransomware attacks, specifically using CVE-2025-0289 to achieve privilege escalation to SYSTEM level, then execute further malicious code,” states the CERT/CC bulletin.
Mitigation and Protection
Paragon Software has released patches, and Microsoft has added vulnerable BioNTdrv.sys versions to its Vulnerable Driver Blocklist. For enterprises, immediate action is crucial:
- Update Paragon Partition Manager: Ensure all systems are updated to the latest patched versions.
- Implement Robust Security Practices: Layer security controls to mitigate the impact of successful exploits. This includes regular patching, strong access controls, and endpoint detection and response (EDR) solutions.
- Monitor for Suspicious Activity: Closely monitor systems for signs of compromise, including unusual process activity and network connections.
- Enable the Microsoft Vulnerable Driver Blocklist: You can check if the blocklist is enabled by going to Settings → Privacy & security → Windows Security → Device security → Core isolation → Microsoft Vulnerable Driver Blocklist and making sure the setting is enabled. This prevents vulnerable drivers from being loaded.
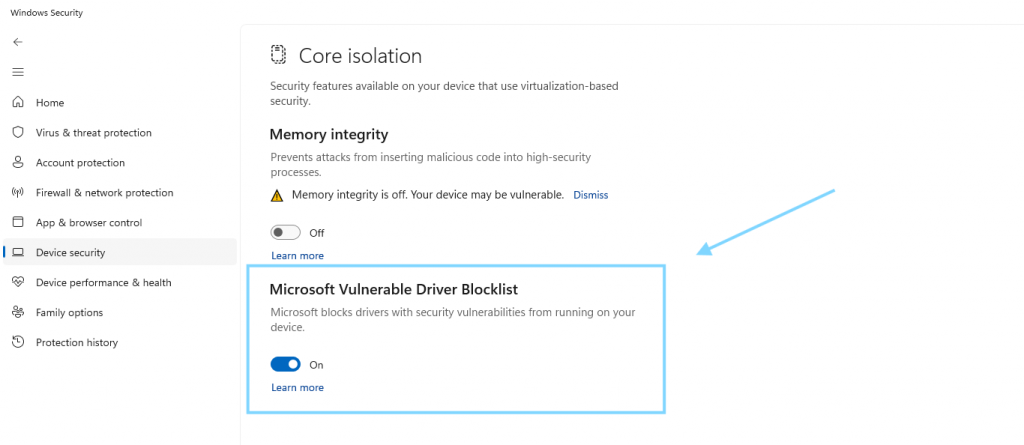
Windows setting for vulnerable drivers blocklist
Source: Daily Security Review
This BYOVD attack highlights the ever-evolving threat landscape. Proactive security measures and rapid response to vulnerabilities are essential for enterprise protection.
Learn more about protecting your organization from ransomware attacks by reading our comprehensive guide on Top 10 Ransomware Groups of 2024. Staying informed about the latest threats is critical for maintaining a strong security posture. For more information on mitigating other types of cyber threats, check out our articles on Phishing Attacks and Data Breaches.