Volt Typhoon’s Resurgence: A Renewed Cyberespionage Threat
The Chinese state-sponsored hacking group, Volt Typhoon, known for its sophisticated cyberespionage operations, has demonstrated its resilience by rebuilding its malware botnet, dubbed KV-Botnet (also known as JDYFJ Botnet by SecurityScorecard), following a disruption by law enforcement in January 2024. This resurgence, detailed in a recent report by SecurityScorecard, highlights the persistent and evolving nature of this significant threat.
Technical Details of the Volt Typhoon Botnet
Volt Typhoon’s primary targets are outdated SOHO (Small Office/Home Office) routers and networking devices. The group’s initial attack vector involved compromising devices such as Netgear ProSAFE firewalls, Cisco RV320s, DrayTek Vigor routers, and Axis IP cameras. This allows them to install custom malware that establishes covert communication and proxy channels, providing persistent access to targeted networks. The malware used is MIPS-based, and the botnet communicates over non-standard ports, making detection more challenging.
The KV-Botnet leverages self-signed SSL certificates, specifically one identified as “jdyfj,” to further obfuscate its activities. SecurityScorecard researchers observed that in just 37 days, Volt Typhoon compromised approximately 30% of all internet-exposed Cisco RV320/325 devices. While the precise vulnerability exploited remains unknown, the researchers emphasized that the end-of-life status of these devices, preventing updates, contributes significantly to their vulnerability. Interestingly, some devices previously infected and cleaned during the January disruption have reappeared in the revived botnet.
The Geography of the Attack and Infrastructure
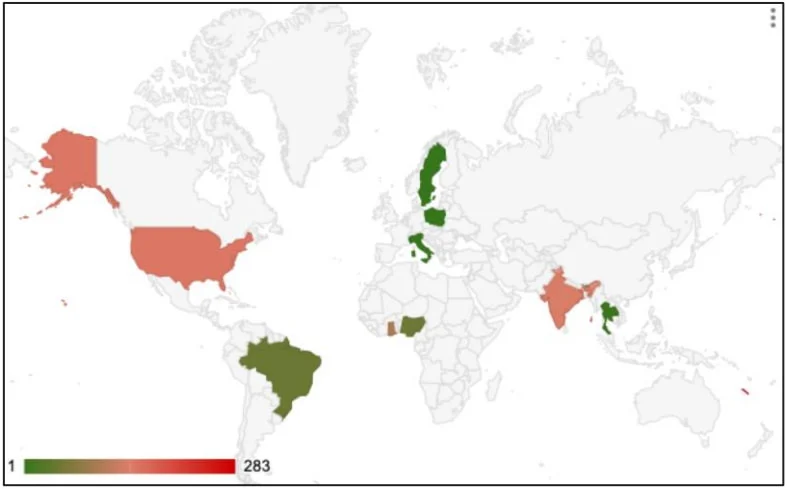
Volt Typhoon infections
Source: SecurityScorecard
The revived Volt Typhoon botnet’s compromised devices are primarily located in Asia. The command and control servers are strategically distributed across Digital Ocean, Quadranet, and Vultr, enhancing the botnet’s resilience and making it more difficult to take down. A particularly intriguing aspect is the use of a compromised VPN device in New Caledonia as a bridge, routing traffic between the Asia-Pacific region and America. SecurityScorecard suggests this is likely a geographically strategic decision by the threat actors.
The main function of the KV-Botnet appears to be the obfuscation of malicious activities by routing traffic through compromised legitimate infrastructure. This sophisticated tactic makes tracing the origin of attacks significantly more difficult.
Volt Typhoon’s Tactics and Persistence
The initial attempt by Volt Typhoon to revive its botnet in February 2024 failed. However, the exploitation of a zero-day vulnerability in August demonstrated the group’s continued activity and capacity for innovation. This latest resurgence confirms their persistence and ability to adapt to countermeasures. The group’s ability to re-establish a significant presence in such a short timeframe underscores the need for proactive security measures.
Mitigating the Volt Typhoon Threat
To protect against Volt Typhoon attacks, SecurityScorecard recommends several crucial steps:
- Replace outdated routers: Older and unsupported router models should be replaced with newer, supported models that receive regular security updates.
- Firewall protection: Place SOHO routers behind firewalls to add an extra layer of security.
- Secure remote access: Avoid exposing remote access to administrative panels directly to the internet.
- Change default credentials: Always change default administrator account credentials on all network devices.
- Update firmware: For newer SOHO routers, install the latest firmware updates to patch known vulnerabilities.
The ongoing activities of Volt Typhoon underscore the persistent threat posed by state-sponsored hacking groups and the importance of robust cybersecurity practices. The group’s ability to rebuild its botnet despite previous disruptions highlights the need for continuous vigilance and adaptation in the fight against sophisticated cyber threats.
The use of end-of-life devices and non-standard communication protocols emphasizes the importance of keeping systems updated and employing advanced threat detection techniques. The geographical spread of the infrastructure and the use of a compromised VPN in New Caledonia as a transit point demonstrate the group’s strategic planning and sophistication. The ongoing threat of Volt Typhoon necessitates a proactive and multi-layered approach to cybersecurity.