A new ransomware strain, identified as VanHelsing ransomware, has emerged, posing significant threats to various systems, including Windows, Linux, BSD, ARM, and ESXi environments. This ransomware-as-a-service (RaaS) operation began promoting itself on underground cybercrime forums on March 7, 2025, allowing experienced affiliates to join for free while requiring a deposit of $5,000 from less experienced threat actors.
Overview of the VanHelsing Ransomware Operation
According to Check Point Research, the VanHelsing ransomware is part of a Russian cybercrime initiative that prohibits attacks on systems within Commonwealth of Independent States (CIS) countries. Affiliates are permitted to retain 80% of the ransom payments, with operators taking the remaining 20%. An automated escrow system facilitates the payments, utilizing two blockchain confirmations for enhanced security.
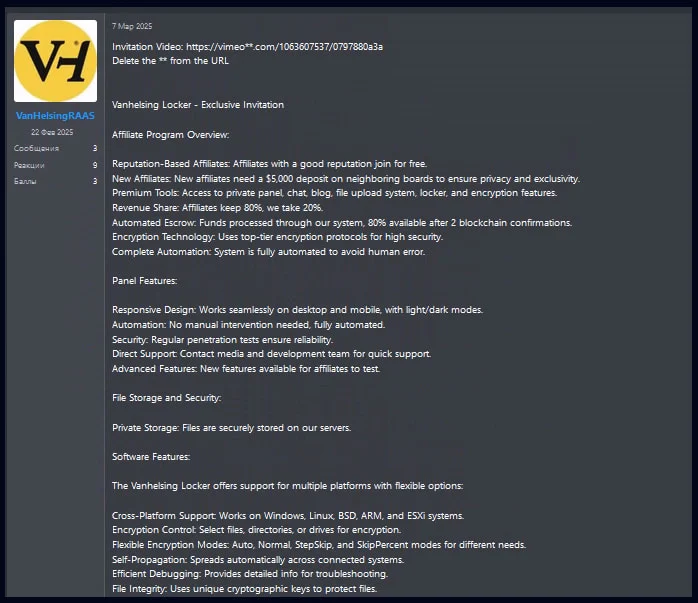
VanHelsing advertisment inviting affiliates to join
Source: Check Point
“Affiliates gain access to a panel with full operational automation, with direct support from the development team,” Check Point analysts reported.
Victims of the VanHelsing ransomware include a city in Texas and two technology companies in the U.S. and France.
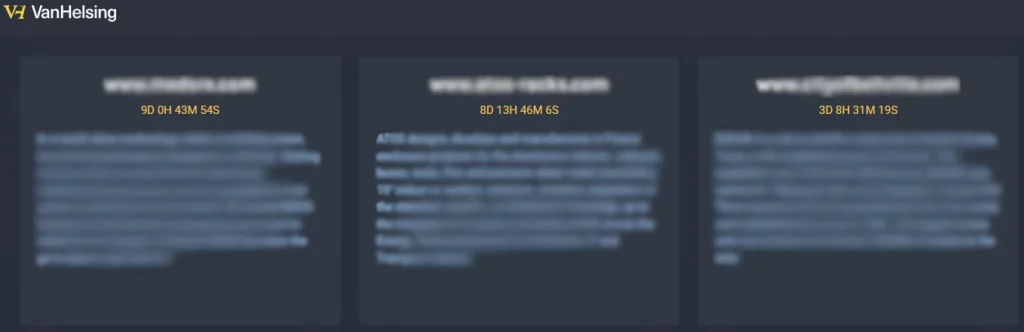
The VanHelsing extortion page
Source: BleepingComputer
The ransomware operators threaten to leak stolen files if their financial demands are not met, with ransom amounts reaching as high as $500,000.
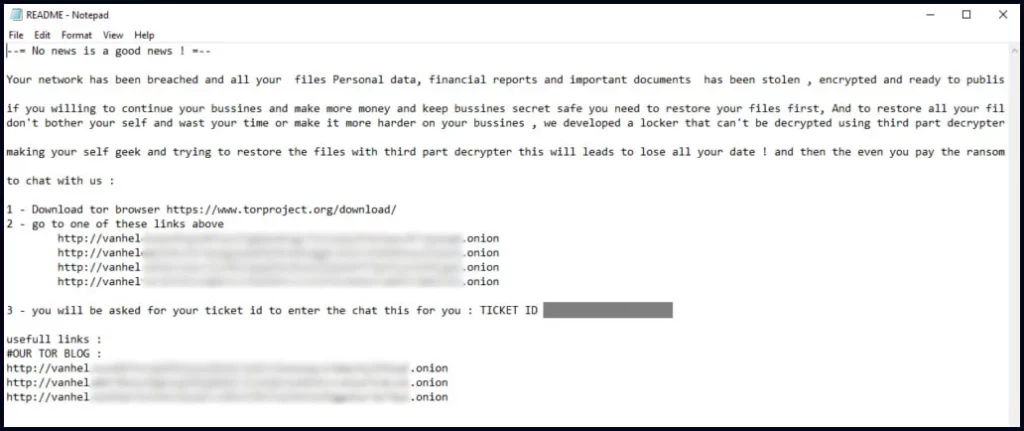
The VanHelsing ransom note
Source: Check Point
Technical Details of VanHelsing Ransomware
The VanHelsing ransomware is written in C++ and was reportedly deployed in the wild for the first time on March 16, 2025. It employs the ChaCha20 algorithm for file encryption, generating a 32-byte (256-bit) symmetric key and a 12-byte nonce for each file. These values are encrypted using an embedded Curve25519 public key, with the resulting encrypted key/nonce pair stored in the encrypted file.
Encryption Process
- Files larger than 1GB: Partially encrypted.
- Smaller files: Fully encrypted.
VanHelsing supports rich command-line interface (CLI) customization, allowing attackers to tailor their strategies for specific victims. This includes:
- Targeting specific drives and folders.
- Restricting the encryption scope.
- Spreading via SMB.
- Skipping shadow copies deletion.
- Enabling a two-phase stealth mode.
In normal encryption mode, the ransomware encrypts file contents and renames files with a .vanhelsing extension. In stealth mode, encryption occurs without immediate renaming, mimicking normal system behavior and reducing the likelihood of detection.
Observations from Check Point Research
Despite its advanced features, Check Point noted several flaws that indicate code immaturity. These include:
- Mismatches in file extensions.
- Errors in exclusion list logic that may lead to double encryption.
- Unimplemented command-line flags.
“VanHelsing remains a worrying rising threat that appears poised to gain traction soon,” Check Point analysts stated.
The emergence of the VanHelsing ransomware highlights the ongoing risks posed by ransomware-as-a-service operations to enterprise businesses. With its sophisticated encryption methods and the potential for significant financial extortion, organizations must remain vigilant against this evolving threat.









