On Christmas Day, the fan expansion called “Downfall” for the indie strategy game Slay the Spire was compromised in the Steam Game Mod Breach.
The Security Breach in Slay the Spire involved the use of the Steam update system to distribute Epsilon information stealer malware.
Developer Michael Mayhem clarified that the compromised package was a standalone modified version of the game, rather than a mod installed through the Steam Workshop.
“One of our devices was hit with malware that did not get flagged or blocked by the security we had running on it. As far as I currently know, it was not a password-stealing malware as 2FA did not trigger or stop this, and of the accounts compromised, all were under different e-mail addresses (and none of those addresses themselves were stolen),”
In a statement to BleepingComputer, Mayhem said that they are
“reluctant to state anything with absolute certainty”
“This has led us to believe it was a token hijack instead (as suggested to us by a security professional), designed specifically to hijack Steam and use it to upload and Discord to prevent warning users, but that at the moment is just speculation.”
Mayhem’s statement to BleepingComputer
At first, it was believed that the attackers successfully breached the Steam and Discord accounts of one of the developers behind Downfall. This unauthorized access enabled them to take control of the mod’s Steam account.
“Update 12/28/23: The email account of the developer was not breached.”
Bleeping Computer states in an update on Steam Game Mod Breach
“The breach window was roughly 1:30 PM-2:30 PM Eastern (1830-1930 UTC+0) on 12/25. If you did launch Downfall on 12/25 during the breach window and got a Unity library installer popup, please continue to read. You may be also at risk. The security breach allowed a malicious upload to replace the Downfall packaged game,”
Mayhem said in a statement.
Details of Steam Game Mod Breach: Epsilon Malware Steals Info and Personal Data
Upon installation on a compromised computer, the malware will gather information such as cookies, saved passwords, credit card details from various web browsers (Google Chrome, Yandex, Microsoft Edge, Mozilla Firefox, Brave, Vivaldi), as well as login information for Steam and Discord.
Additionally, it will seek out documents with filenames containing the term ‘password’ and search for further credentials, including local Windows login and Telegram. Users of Downfall are strongly advised to change all significant passwords, particularly those for accounts lacking 2-factor authentication (2FA).
According to reports from affected users, the malicious update would install the malware in either the AppData folder as a Windows Boot Manager application or in the /AppData/Roaming folder as UnityLibManager.
Epsilon Stealer, the type of malware involved, is a known information-stealing malware that is available for purchase on platforms like Telegram and Discord. It is frequently used by threat actors to target gamers on Discord, enticing them to install the malware by offering payment in exchange for testing a new game for bugs.
Upon installation of the game, the malware is covertly activated and operates surreptitiously, extracting sensitive user information such as passwords, credit card details, and authentication cookies.
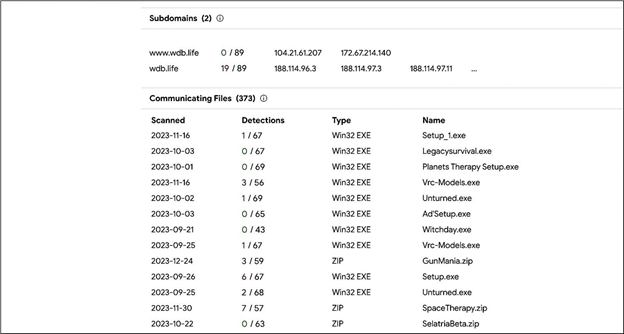
The threat actors then employ this pilfered data to either compromise additional accounts or vends it on illicit dark web marketplaces. The VirusTotal data indicates a high probability that the perpetrator responsible for this attack has also targeted other games and game developers in the past.
Steam Tightens Security After the Breach
Valve, the company behind Steam, made an important announcement in October. They introduced a new requirement for game developers to undergo SMS-based security checks when pushing updates on the default release branch on Steam.
This decision was prompted by a series of incidents starting in late August, where compromised Steamworks accounts were used to distribute harmful game builds, infecting players with malware.
“As part of a security update, any Steamworks account setting builds live on the default/public branch of a released app will need to have a phone number associated with their account so that Steam can text you a confirmation code before continuing,”
“The same will be true for any Steamworks account that needs to add new users. This change will go live on October 24, 2023, so be sure to add a phone number to your account now. We also plan on adding this requirement for other Steamworks actions in the future.”
Valve said in October