Cybercriminals are carrying out sophisticated fraud schemes by impersonating legitimate companies to steal high-value equipment such as network gear, medical devices, and computers. Proofpoint researchers have uncovered a widespread scam in which threat actors pose as corporate procurement agents, using stolen business credentials to order goods on credit and then vanish before payments are due.
“These actors use a network of shipping forwarding services, standalone warehouses, and individual money mules to enable their crimes,” said Proofpoint in its threat report.
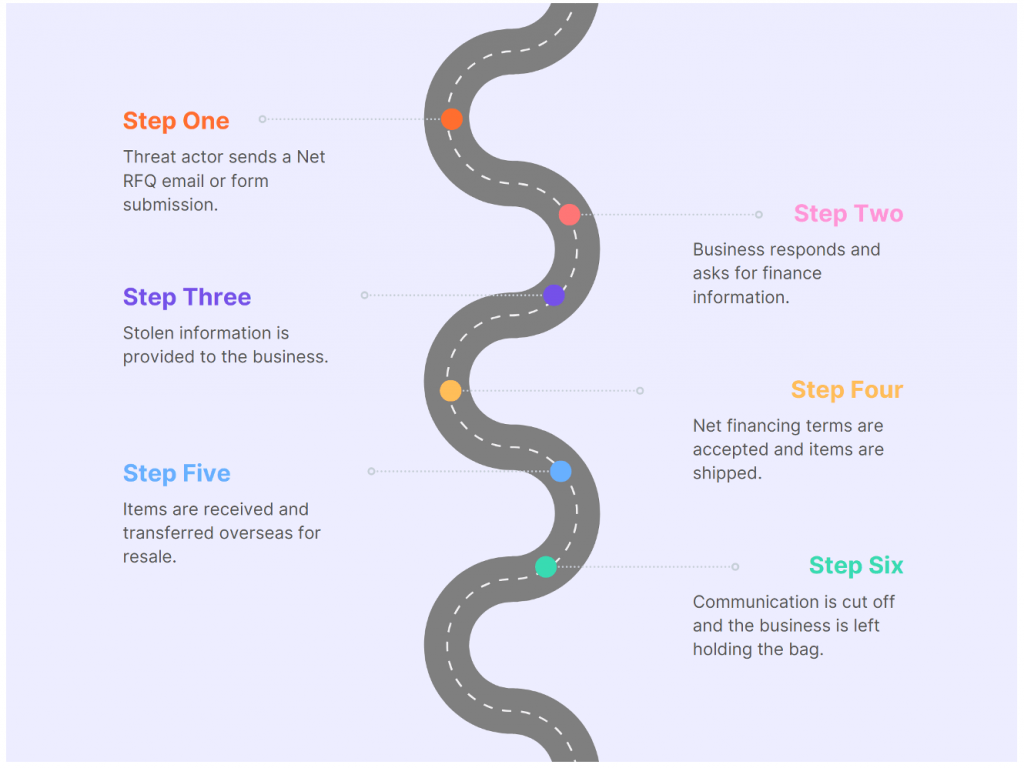
The scheme primarily revolves around Net RFQ (Request for Quote) scams, where the attackers leverage common business financing practices that allow companies to buy products now and pay within 15 to 90 days. By the time the scam is discovered, the fraudsters have already disappeared with the goods—leaving vendors unpaid and business identities misused.
Source: Proofpoint
How Corporate Identity Theft Powers This Fraud
The scam begins with cybercriminals researching legitimate companies—often using public records or stolen employee data—to create fake procurement agents. They replicate corporate branding and build credible email identities using:
- Real Employer Identification Numbers (EINs)
- Data Universal Numbering System (DUNS) identifiers
- Publicly available business documentation
- Stolen names and roles of actual employees
These emails are convincing, complete with formal signatures and branding elements to mimic genuine company communications.
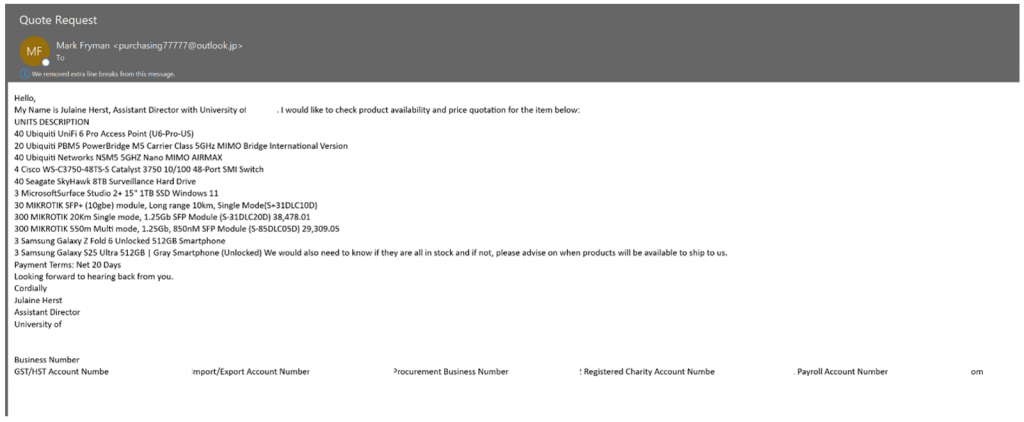
In one example cited by Proofpoint, scammers impersonated a well-known university and requested quotes for dozens of Ubiquiti UniFi 6 Pro access points, hundreds of MIKROTIK SFP modules, and other high-demand networking gear.
Source: Proofpoint
The attackers typically:
- Use free email accounts or domains resembling real company names
- Request specific items that are in global demand, especially in developing countries
- Offer all necessary documentation for Net-30 or Net-60 payment terms
- Try to rush shipments and sometimes reduce the order size to speed up approval
“The scammers are usually keen to get the shipment started as soon as possible,” researchers noted.
Frequently Targeted Products and Services
The goods requested are typically expensive and easy to resell. According to the research, some of the most frequently requested equipment includes:
- Fluke brand electronic testing tools
- Surveillance cameras
- Wi-Fi and network infrastructure
- Hard drives and storage devices
- Marine GPS units and satellite phones
- Medical diagnostic or monitoring devices
These high-value products are commonly targeted due to their global resale value, especially in regions like West Africa.
Scam Tactics and Delivery Logistics
After securing a quote and approval, scammers delay providing shipping addresses until just before dispatch. This step allows them to:
- Finalize arrangements with freight forwarders or mules
- Ensure operational security by reducing the risk of early detection
- Use residential addresses or short-term rented warehouses for delivery
Proofpoint’s findings show that:
- Threat actors frequently use shipping forwarding companies that unknowingly help transport goods abroad, mainly to Ghana and Nigeria
- Criminals rent 10’x15’ or 15’x20’ storage units on short-term leases across the U.S. to collect goods
- Several fraudulent deliveries were intercepted, and 19 scam domains were taken down due to ongoing investigations
Some of the fraudulent domains included:
novartispharmaceuticalscorp[.]comhbfullercompany[.]netmagnetek-inc[.]comamericaninstituteresearch[.]orgabec-electricinc[.]com
Despite domain takedowns, the attackers often spin up new lookalike websites to continue the fraud seamlessly.
Social Engineering Lures and Business Email Fraud
Beyond physical goods theft, these scams open the door for other types of attacks:
- Malware deployment
- Phishing schemes
- Business Email Compromise (BEC)
- Social engineering exploits targeting vendor communication chains
Fake quote requests are now among the top five social engineering tactics targeting businesses, according to Proofpoint.
“Search the company name online; does the domain match the sender’s domain? Is the email legitimate?” the researchers advised.
“Phoning the business directly from a number listed on their official website can help validate whether something is authentic, or if it’s a scam.”
Enterprises are urged to exercise heightened scrutiny toward any net financing request that involves urgency or irregular communication behavior.









