The Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning regarding a recently detected vulnerability in Roundcube email servers. This vulnerability, which was patched in September, is now being actively exploited through cross-site scripting (XSS) attacks.
Roundcube Email Server Bug (CVE-2023-43770) is a Persistent XSS Bug
The specific security flaw, identified as CVE-2023-43770, is categorized as a persistent XSS bug. This allows attackers to gain unauthorized access to restricted information by exploiting maliciously crafted links in plain text messages. It’s important to note that these attacks are relatively simple and require user interaction.
Roundcube email servers running versions newer than 1.4.14, 1.5.x before 1.5.4, and 1.6.x before 1.6.3 are susceptible to this vulnerability.
It is crucial for organizations utilizing Roundcube email servers to promptly update to the latest patched versions in order to mitigate the risk of exploitation.
“We strongly recommend to update all productive installations of Roundcube 1.6.x with this new version,”
The Roundcube security team.
Roundcube Webmail XSS Vulnerability Added to CISA’s KEV
CISA has included the Roundcube email server vulnerability in its Known Exploited Vulnerabilities Catalog, emphasizing the significant risks it poses to federal agencies.
While specific details about the attacks are not provided, CISA has instructed U.S. Federal Civilian Executive Branch agencies to secure their Roundcube webmail servers against this vulnerability within three weeks, as mandated by a binding operational directive.
Although the catalog primarily targets federal agencies, it is strongly recommended that private organizations worldwide also prioritize addressing this security flaw.
Shodan, a search engine for internet-connected devices, currently identifies over 132,000 Roundcube servers accessible online. However, there is no available information regarding the number of servers that may be vulnerable to ongoing attacks exploiting the CVE-2023-43770 vulnerability.
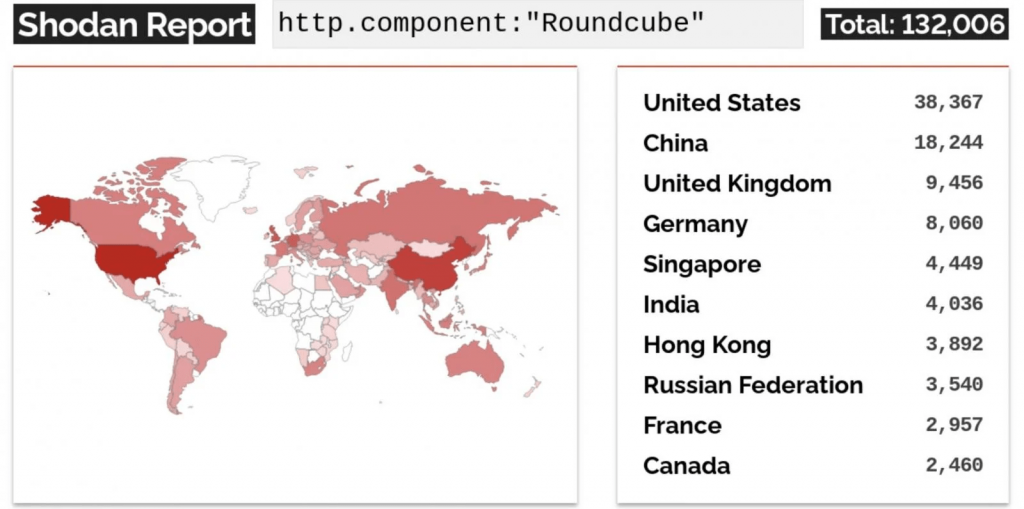
Source: Shodan
Another Roundcube Vulnerability CVE-2023-5631 Exploited by TA473
Another recently discovered vulnerability in Roundcube, identified as CVE-2023-5631, has been exploited as a zero-day by the Winter Vivern (aka TA473) Russian hacking group since at least October 11.
The attackers employed HTML email messages containing specifically crafted malicious SVG documents to remotely inject arbitrary JavaScript code.
By leveraging this vulnerability, the Russian hackers were able to deploy a JavaScript payload in their October attacks, enabling them to pilfer emails from compromised Roundcube webmail servers owned by government entities and think tanks in Europe.
In addition to the recently exploited Roundcube vulnerability (CVE-2023-5631), the Winter Vivern operators have also exploited the CVE-2020-35730 Roundcube XSS vulnerability between August and September 2023.
It is worth noting that the Russian APT28 cyber-espionage group, which is associated with Russia’s General Staff Main Intelligence Directorate (GRU), also utilized the same vulnerability to breach Roundcube email servers belonging to the Ukrainian government.
Furthermore, the Winter Vivern hackers targeted NATO countries in early 2023 by exploiting the Zimbra CVE-2022-27926 XSS vulnerability. This allowed them to gain unauthorized access to emails belonging to NATO governments, officials, and military personnel.