Oracle has privately acknowledged a data breach affecting a legacy environment, confirming the theft of old client credentials. While Oracle downplays the sensitivity of the stolen data, a threat actor has shared samples, proving the breach’s validity.
The attacker exploited a 2020 Java vulnerability to access Oracle Cloud Classic servers, exfiltrating data from the Oracle Identity Manager (IDM) database. This included user emails, hashed passwords, and usernames.
The threat actor, known as rose87168, offered 6 million records for sale on BreachForums. Despite initial denials, Oracle confirmed the breach to some clients, stating that the compromised system was a legacy platform, Oracle Cloud Classic. However, the company’s statements have been criticized for downplaying the severity of the incident. A separate breach at Oracle Health, impacting patient data, further compounds concerns.
Details of the Oracle Cloud Breach
The breach involved Oracle’s “legacy environment,” specifically Oracle Cloud Classic (Gen 1), last used in 2017. according to CybelAngel, the attacker leveraged a 2020 Java exploit to deploy a web shell and additional malware.
Data exfiltration targeted the Oracle Identity Manager (IDM) database, compromising user emails, hashed passwords, and usernames. The threat actor, rose87168, posted samples of the stolen data on BreachForums, including LDAP information and a list of affected companies.
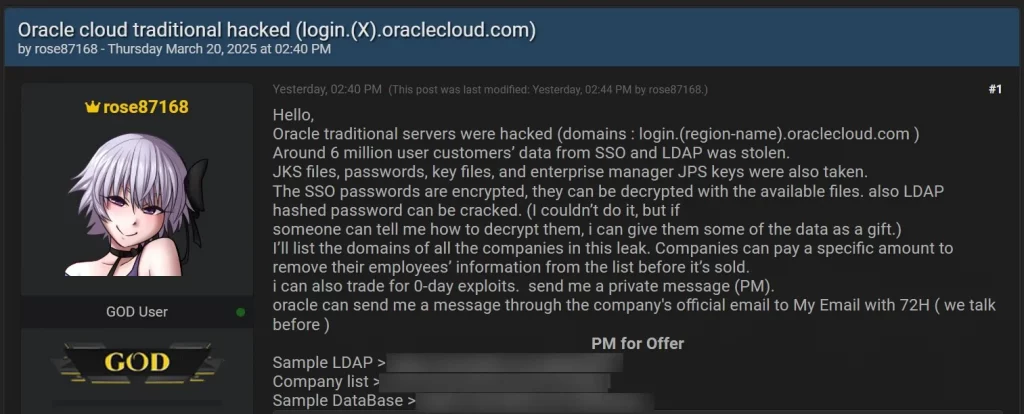
Threat actor selling data allegedly stolen from Oracle Cloud
Source: (BleepingComputer)
Oracle initially denied a cloud breach, claiming the credentials were not for Oracle Cloud and that no customers experienced data loss. However, BleepingComputer says that it has independently verified the authenticity of leaked data samples provided by the threat actor. This included LDAP display names, email addresses, given names, and other identifying information.
Cybersecurity expert Kevin Beaumont explained Oracle’s denial strategy: “Oracle rebadged old Oracle Cloud services to be Oracle Classic. Oracle Classic has the security incident. Oracle are denying it on ‘Oracle Cloud’ by using this scope — but it’s still Oracle cloud services that Oracle manage. That’s part of the wordplay.”
The Oracle Health Breach
A separate incident involved Oracle Health (formerly Cerner). This breach impacted multiple U.S. healthcare organizations and hospitals, resulting in the theft of patient data. The attackers used compromised customer credentials to access legacy Cerner data migration servers. The threat actor, “Andrew,” is now extorting impacted hospitals, demanding millions of dollars in cryptocurrency to prevent data leaks.
Oracle’s Response and Ongoing Investigations
Oracle has confirmed the breach to some customers but maintains its public stance denying a broader Oracle Cloud compromise. The company has engaged CrowdStrike and the FBI to investigate the incidents. The ongoing investigations and the lack of full transparency from Oracle remain a significant concern for enterprise clients.









