A newly discovered malware campaign, dubbed “MassJacker,” is leveraging a staggering 778,531 cryptocurrency wallet addresses to steal digital assets. This sophisticated operation, uncovered by CyberArk, utilizes clipboard hijacking techniques to silently redirect cryptocurrency transactions, highlighting a concerning evolution in malware tactics.
The Mechanics of MassJacker Malware
MassJacker operates as a clipboard hijacker, also known as a “clipper.” This type of malware monitors the Windows clipboard for copied cryptocurrency wallet addresses. When a user copies an address, MassJacker stealthily replaces it with one controlled by the attackers. The victim, unaware of the manipulation, unknowingly sends their funds to the malicious actors. The simplicity and effectiveness of this method make it particularly difficult to detect.
Scale and Financial Impact
While CyberArk’s analysis revealed approximately $95,300 in 423 wallets directly linked to the campaign, the true financial impact is likely much higher. Historical data suggests significantly larger transactions, and a central Solana wallet used by the attackers has amassed over $300,000. The sheer number of compromised wallets (778,531) indicates a wide-reaching and potentially devastating impact.
Attribution and Operational Model:
CyberArk suspects a single threat group is behind MassJacker, citing consistent file names and encryption keys across the campaign. However, the possibility of a malware-as-a-service (MaaS) model cannot be ruled out, where a central administrator sells access to the malware to other cybercriminals. This model allows for wider distribution and increased profitability for the threat actors.
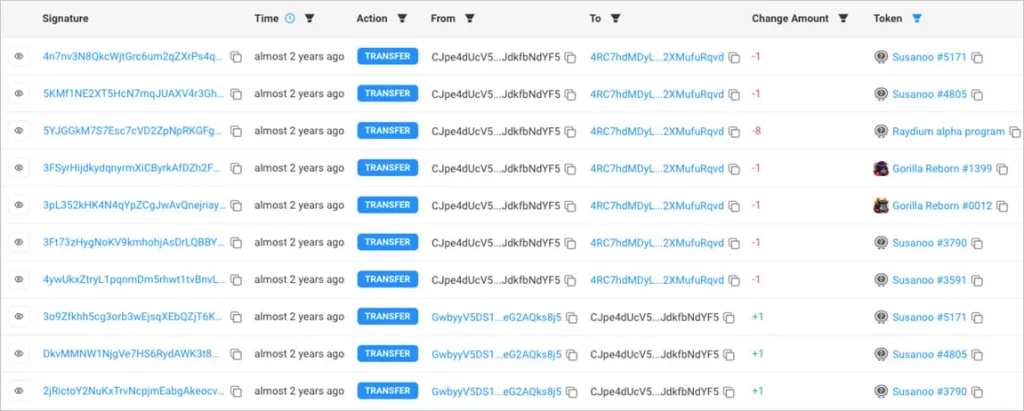
Transactions on the Solana wallet
Source: CyberArk
Distribution and Technical Details:
The recently discovered MassJacker malware campaign represents a significant threat to cryptocurrency users, employing a sophisticated combination of techniques to steal digital assets from compromised computers. This analysis delves into the technical intricacies of the malware, revealing its advanced evasion and persistence mechanisms.
Infection Chain and Payload Delivery:
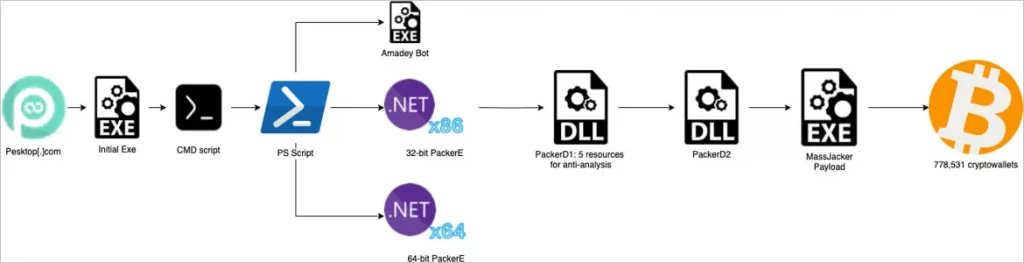
MassJacker infection chain
Source: CyberArk
MassJacker’s distribution relies on the malicious website pesktop[.]com, a known source of pirated software and malware. The infection chain begins when a user downloads and executes a seemingly legitimate software installer. This installer, however, contains a concealed cmd script that triggers a PowerShell script. This script acts as a downloader, fetching the Amadey bot and two crucial loader files: PackerE and PackerD1.
Amadey acts as an initial stage, launching PackerE. PackerE’s primary function is to decrypt and load PackerD1 into memory. PackerD1 is a highly obfuscated component, employing several advanced anti-analysis techniques. These include:
- Just-In-Time (JIT) Hooking: This technique dynamically alters the behavior of system functions, making reverse engineering and analysis significantly more challenging.
- Metadata Token Mapping: This obfuscation method alters the names and structures of functions, making it difficult to understand the code’s functionality.
- Custom Virtual Machine: Instead of executing standard .NET code, PackerD1 utilizes a custom virtual machine for command interpretation. This adds another layer of complexity, hindering analysis efforts.
PackerD1 then decrypts and injects PackerD2. PackerD2’s role is to decompress and extract the final payload—MassJacker itself—before injecting it into the legitimate Windows process InstalUtil.exe. This process injection technique allows MassJacker to operate with elevated privileges and evade detection by security software.
Clipboard Hijacking and Wallet Address Replacement:
The core functionality of MassJacker revolves around its clipboard hijacking capabilities. The malware utilizes regular expression (regex) patterns to monitor the Windows clipboard for cryptocurrency wallet addresses. When a match is found, MassJacker replaces the legitimate address with one from an encrypted list of attacker-controlled wallets. This list is likely stored within the malware itself or fetched from a command-and-control (C2) server. The replacement is seamless and undetectable to the user, leading to the unwitting transfer of funds.
Evasion and Persistence Techniques:
Beyond the obfuscation techniques within PackerD1, MassJacker likely employs additional evasion techniques to remain undetected. These may include:
- Network Obfuscation: Communication with the C2 server might be encrypted and obfuscated to avoid detection by network monitoring tools.
- Rootkit Capabilities: The malware might contain rootkit-like functionalities to hide its presence from system processes and security tools.
- Anti-Debugging Techniques: MassJacker may incorporate anti-debugging measures to prevent security researchers from analyzing it in a debugger environment.
The MassJacker campaign highlights the ongoing evolution of malware tactics and the increasing sophistication of cybercriminal operations. The use of clippers, while seemingly simple, proves highly effective in stealing cryptocurrency. CyberArk urges the cybersecurity community to investigate large-scale cryptojacking operations like MassJacker, as they may provide valuable insights into the identities and methods of numerous threat actors. The seemingly modest financial gains from individual victims mask the substantial overall impact of such widespread attacks.
Key Takeaways:
- Clipboard Hijacking: MassJacker uses clipboard hijacking to steal cryptocurrency.
- Massive Scale: Over 778,000 wallets are potentially affected.
- Sophisticated Obfuscation: The malware employs advanced techniques to evade detection.
- Financial Impact: While initial analysis shows limited funds, the actual amount is likely significantly higher.
- Threat Actor Attribution: While a single group is suspected, a MaaS model is also possible.
Helpful Reads: