A recent report has revealed that over 44,000 IP addresses were infected with the Latrodectus malware, a powerful downloader used by threat actors to launch ransomware and banking trojans. The discovery came just ahead of Operation Endgame, a coordinated global law enforcement action targeting major malware delivery infrastructures.
What Is Latrodectus and Why Is It Dangerous?
Latrodectus is a Windows-based malware downloader active since at least 2023. It’s used by cybercriminals to install a range of secondary payloads on infected machines. These payloads often include:
- IcedID, a modular banking trojan designed to steal financial data
- QakBot, another banking trojan with botnet capabilities
- Pikabot, a backdoor used for initial system access
- Other ransomware loaders and infostealers
Latrodectus is typically delivered via malicious email campaigns. Once inside a system, it communicates with command-and-control (C2) servers, sharing system information and awaiting further instructions. Proofpoint researchers highlight its sandbox evasion techniques, which make it difficult for traditional testing environments to detect.
“This special report has severity level CRITICAL set on all events.” — Shadowserver Foundation
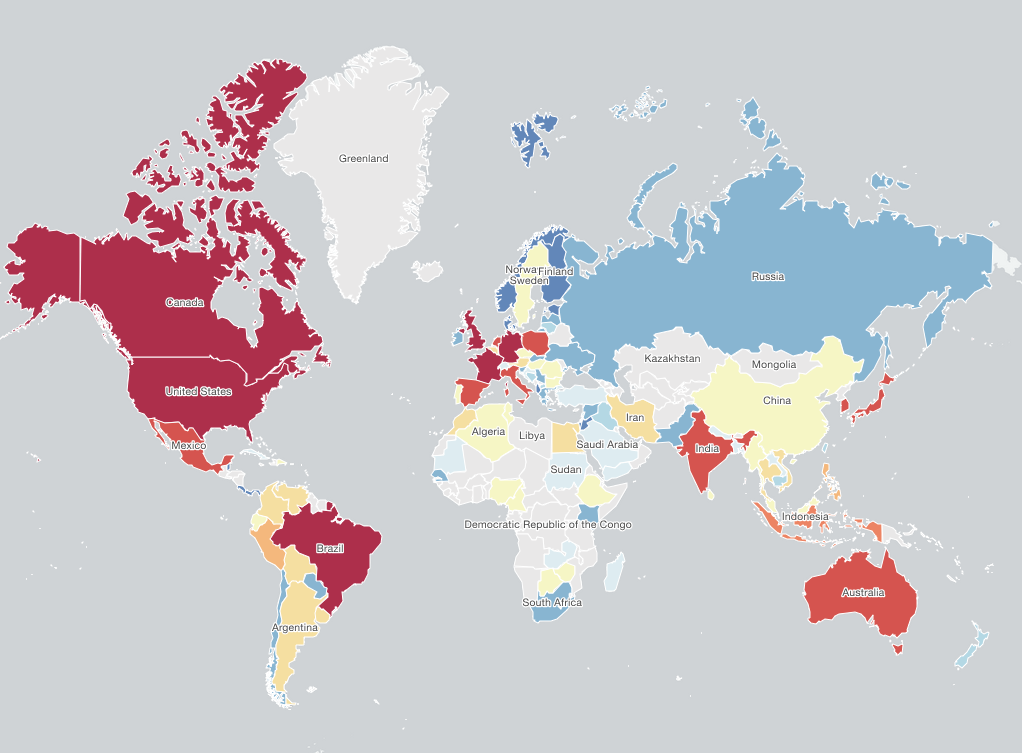
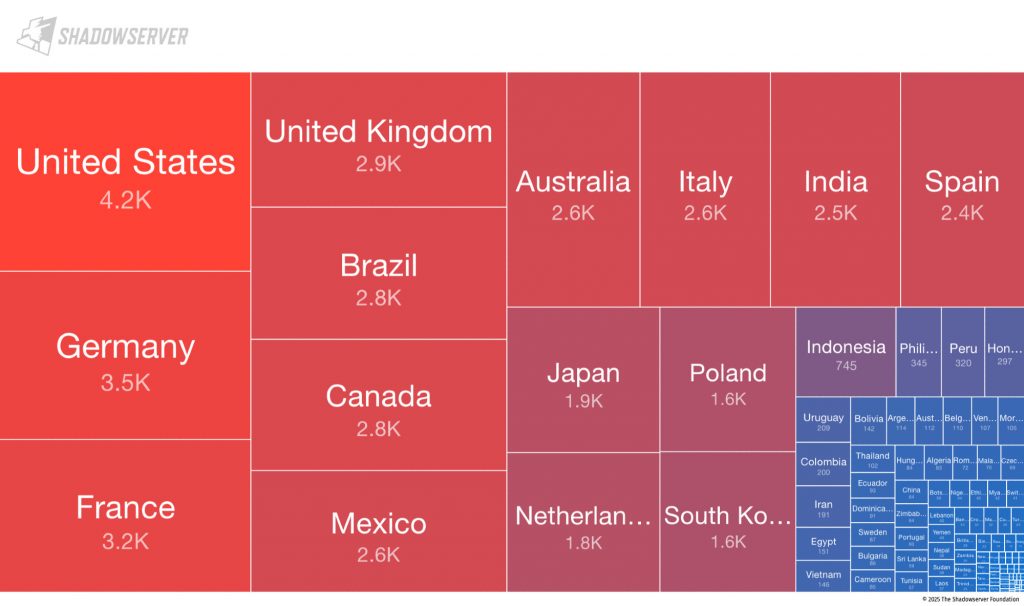
Infection Data Collected Between April and May 2025
The Shadowserver Foundation, a nonprofit cybersecurity group, published a special report documenting infections detected between April 26 and May 20, 2025. According to their analysis:
- United States: 4,200 infected IPs
- Germany: 3,500
- France: 3,200
- United Kingdom: 2,900
- Brazil: 2,800
- Over 2,000 hosts each in Canada, Mexico, Australia, Italy, India, and Spain
Shadowserver received the data from law enforcement partners involved in Operation Endgame, sharing it with ISPs, network owners, and national CERTs to help remediate infections.
Operation Endgame Targets Malware Infrastructure Worldwide
Operation Endgame is a long-term, global law enforcement initiative aimed at dismantling the infrastructure that supports ransomware and other malware campaigns. On May 23, 2025, Europol reported a major milestone:
- 300 servers seized
- 650 domains taken down
- 20 arrest warrants issued
- Multiple malware strains neutralized, including:
- Latrodectus
- Bumblebee
- QakBot
- HijackLoader
- DanaBot
- Trickbot
- Warmcookie
Despite these takedowns, devices previously infected by Latrodectus may still pose a risk. Shadowserver warns that many of the 44,000+ IPs could still be running malicious modules, some of which may continue to exfiltrate data or await new payloads.
Key Takeaways for Enterprise Security Teams
- Latrodectus is still a live threat despite the takedown, with many infected machines potentially uncleaned.
- Its use as a delivery platform for banking trojans and ransomware makes it a critical risk vector.
- Operation Endgame’s data is now being used to help enterprises and CERTs isolate and clean up infections.
Enterprises should verify if any of their systems or IP ranges are listed in Shadowserver’s data and take immediate remediation steps if so.