A recent release of confidential documents from a Chinese hacking contractor iSoon Leaks data that reveals a workforce that is dissatisfied and underpaid, but still managed to infiltrate numerous regional governments and potentially even NATO.
GitHub Data Leaks from iSoon Poses Serious Implications for Espionage
A significant breach of data has been discovered on GitHub, originating from iSoon (also known as Anxun), a private industry contractor of the Chinese Ministry of Public Security (MPS).
This GitHub leak has exposed a considerable amount of sensitive information, which could have serious implications for espionage activities.
The alleged MPS data leak contained various types of information, such as spyware, details about espionage operations, and even mentions of a supposed “Twitter Monitoring Platform”. This breach in MPS data resembles the scale of the NTC Vulkan leak, highlighting the seriousness and potential repercussions of the incident.
Source: GitHub
The leaked documents, which are claimed to be internal Chinese government files, emerged on GitHub, raising concerns about the security measures within the MPS system. However, it is important to note that the authenticity of these documents has not been verified.
The Cyber Express has made contact with the Chinese Ministry of Public Security to gather more information regarding the MPS data breach. As of now, there has been no official acknowledgement or clarification from the Ministry, leaving the claims surrounding the breach unverified.
The leaked messages exposed conversations and operational details involving different entities, providing some insight into potentially sensitive information. Although the specific contents of these exchanges are still being examined, they suggest the magnitude and intricacy of the breach.
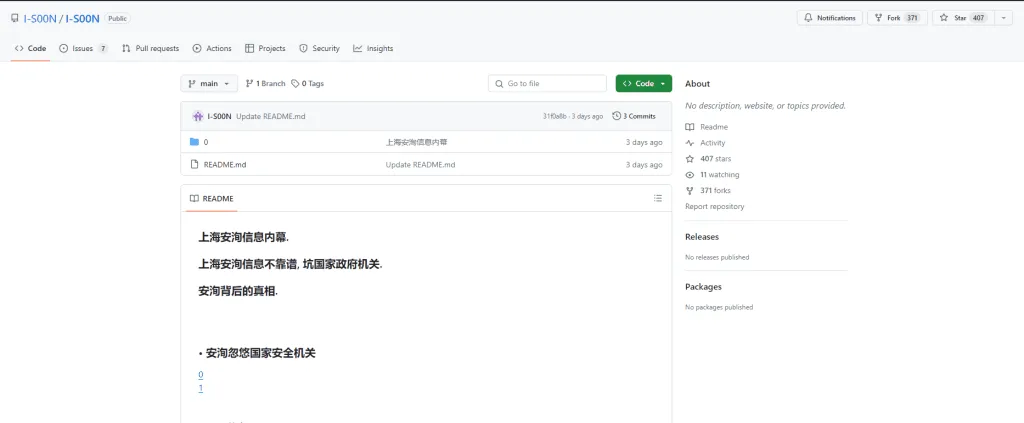
The iSoon Leaks Data Consisted of 66 links Stored in a GitHub Repository Called I-S00N
The individual responsible for this significant breach made claims stating, “上海安洵信息内幕. 上海安洵信息不靠谱, 坑国家政府机关. 安洵背后的真相. 安洵忽悠国家安全机关,” which translates to “Shanghai Anxun Information Insider. Shanghai Anxun’s information is unreliable and is a trap for national government agencies. The truth behind An Xun.”
Furthermore, the data revealed an extensive collection of conversations, reports, official government plans, articles, phone numbers, names, and contact information, spread across numerous folders within the logs, amounting to a substantial volume of information.
GitHub Data Leak Information Listed in the MPS Data Leak
Source: GitHub
The individual responsible for the leaked data has organized it into specific sections. The data from links 0-1 discusses how An Xun deceived the national security agency. The subsequent set of data, spanning links 2-10, consists of employee complaints.
Links 11-13 contain information regarding An Xun’s financial troubles. Link 14 is dedicated to chat records between An Xun’s top boss, Wu Haibo, and his second boss, Chen Cheng.
Links 15-20 focus on the topic of “Anxun low-quality products,” while links 21-28 reveal information about An Xun’s product portfolio. From links 39 to 60, there is discussion about An Xun’s infiltration into government departments overseas, including those of India, Thailand, Vietnam, South Korea, NATO, and others.
Additionally, the remaining links, from 61 to 65, contain data pertaining to An Xun employee information.
Within these logs, there were exchanges of data, collaborations with various departments or entities, project assessments, coordination for events like competitions or training sessions, as well as negotiations related to the sale or sharing of information.
The conversations also addressed challenges such as resource allocation, concerns about pricing and quality, and difficulties in communication with certain contacts.
Furthermore, an intriguing aspect of the conversations within this MPS data breach is that the logs date back to 2018 and encompass a significant amount of sensitive information involving multiple vendors from China and other nations.