The internet archive breach has exposed the personal data of 31 million users, highlighting the vulnerability of even seemingly secure online platforms.
The cyber attack represents a major security incident, impacting the renowned online archive known for its Wayback Machine. The scale of the internet archive hack is alarming, underscoring the critical need for robust cybersecurity measures across all digital platforms.
The attack on , discovered on October 9th, 2024, involved the compromise of a user authentication database containing sensitive information. The data breach, initially signaled by a JavaScript alert displayed on the archive.org website, revealed the extent of the data theft.
The alert, created by the hacker, boldly proclaimed: “Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!”
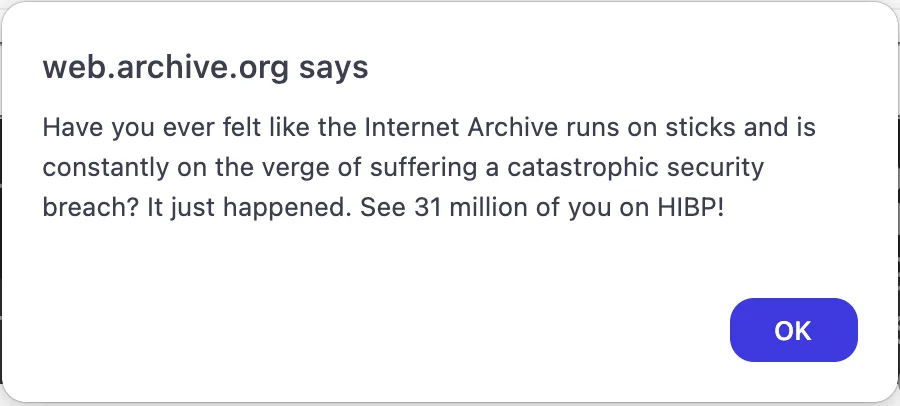
JavaScript alert shown on Archive.org
Source: BleepingComputer
This brazen message pointed users towards Have I Been Pwned (HIBP), a data breach notification service.
Technical Details of the Internet Archive Breach
The stolen data, a 6.4GB SQL file named “ia_users.sql,” was shared with HIBP nine days prior to the public disclosure. Troy Hunt, the creator of HIBP, confirmed the authenticity of the data. The database contained crucial authentication information for 31 million registered members. This compromised data included:
- Email addresses
- Screen names
- Password change timestamps
- Bcrypt-hashed passwords
- Other internal data
The most recent timestamp on the stolen records was September 28th, 2024, indicating the likely date of the internet archive breach. The compromised passwords, while hashed using the bcrypt algorithm, still pose a significant risk, especially considering the age of some passwords. The use of bcrypt, while strong, doesn’t negate the risk entirely, particularly if passwords were weak or reused across multiple platforms.
The authenticity of the data was verified by contacting users listed in the database. Security researcher Scott Helme confirmed that his compromised record accurately reflected his password information and change timestamps. A sample record provided was:
9887370, internetarchive@scotthelme.co.uk,$2a$10$Bho2e2ptPnFRJyJKIn5BiehIDiEwhjfMZFVRM9fRCarKXkemA3Pxu,ScottHelme,2020-06-25,2020-06-25,internetarchive@scotthelme.co.uk,2020-06-25 13:22:52.7608520,\N0\N\N@scotthelme\N\N\N
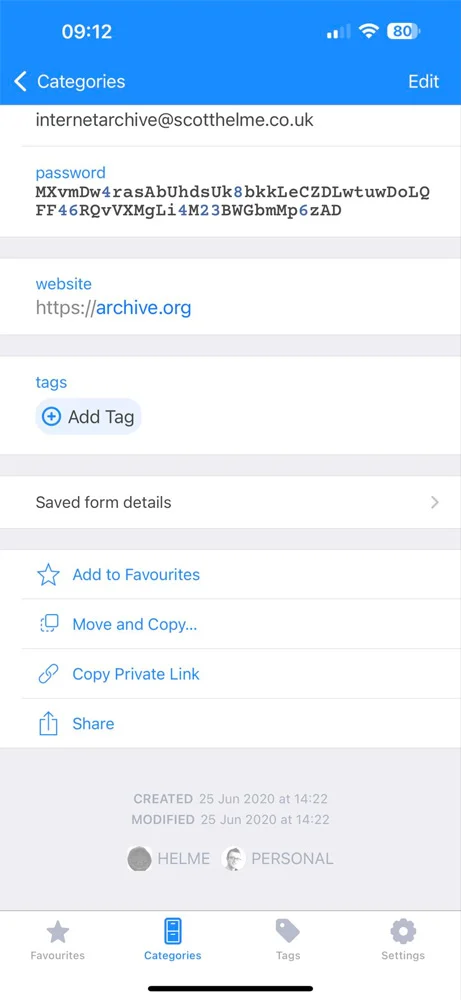
Password manager entry for archive.org
Source: Scott Helme
This internet archive attack highlights the importance of strong password management practices and the use of unique, complex passwords for each online account.
The Aftermath of the Internet Archive Hack
Troy Hunt contacted the Internet Archive three days before the public disclosure, initiating a responsible disclosure process. However, he received no response.
The internet archive breach incident also coincided with a Distributed Denial of Service (DDoS) attack against the Internet Archive, claimed by the BlackMeta hacktivist group. While the Internet Archive founder, Brewster Kahle, confirmed both the data breach and the DDoS attacks, he stated that they were not believed to be connected.
Kahle’s statement on X (formerly Twitter) detailed the situation: “What we know: DDOS attacked—fended off for now; defacement of our website via JS library; breach of usernames/email/salted-encrypted passwords,” and “What we’ve done: Disabled the JS library, scrubbing systems, upgrading security.”
Subsequent DDoS attacks temporarily took archive.org and openlibrary.org offline.
The internet archive breach and subsequent DDoS attacks raise serious questions about the security posture of large online archives and the potential impact of such breaches on millions of users. The incident serves as a stark reminder of the ongoing need for robust security measures and the importance of responsible data handling practices.
The long-term consequences of this internet archive hack remain to be seen, but the immediate impact on user trust and data security is undeniable. The investigation into the root cause of the internet archive attack is ongoing, and further updates are expected. Users are urged to monitor HIBP for updates and to take necessary steps to protect their accoun









