The Interlock ransomware group, a rapidly evolving cybercriminal threat, has intensified its operations against critical infrastructure sectors across North America and Europe, prompting a joint advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the FBI, and the Department of Homeland Security (DHS).
First emerging in late 2024, the Interlock group has quickly established itself as a serious actor in the ransomware ecosystem. Despite being relatively new, the gang has launched numerous high-impact attacks, most notably targeting healthcare and education sectors with devastating effect. According to the latest #StopRansomware alert released on Tuesday, Interlock’s ongoing campaigns reveal a mix of technical innovation, strategic deception, and increasing aggression.
“These actors are opportunistic and financially motivated in nature and employ tactics to infiltrate and disrupt the victim’s ability to provide their essential services,” CISA stated.
Interlock’s Methods: RATs, Fake Updates, and ClickFix Social Engineering
The group’s initial access tactics differ from typical ransomware operators. According to the FBI, Interlock deploys drive-by downloads through legitimate but compromised websites. These payloads are disguised as browser updates—most often fake Google Chrome or Microsoft Edge prompts.
Additionally, the attackers employ a social engineering method dubbed the “ClickFix” technique. Victims are lured with fake reCAPTCHA pages that instruct them to launch a malicious PowerShell command via the Windows Run prompt. This leads to the deployment of a remote access trojan (RAT), which lays the groundwork for deeper infiltration.
Recent campaigns have introduced a resilient PHP-based variant of the Interlock RAT—an evolution from the JavaScript-based version observed previously. This new variant is believed to be part of a broader campaign named “Kongtuke FileFix,” which surfaced in June 2025.
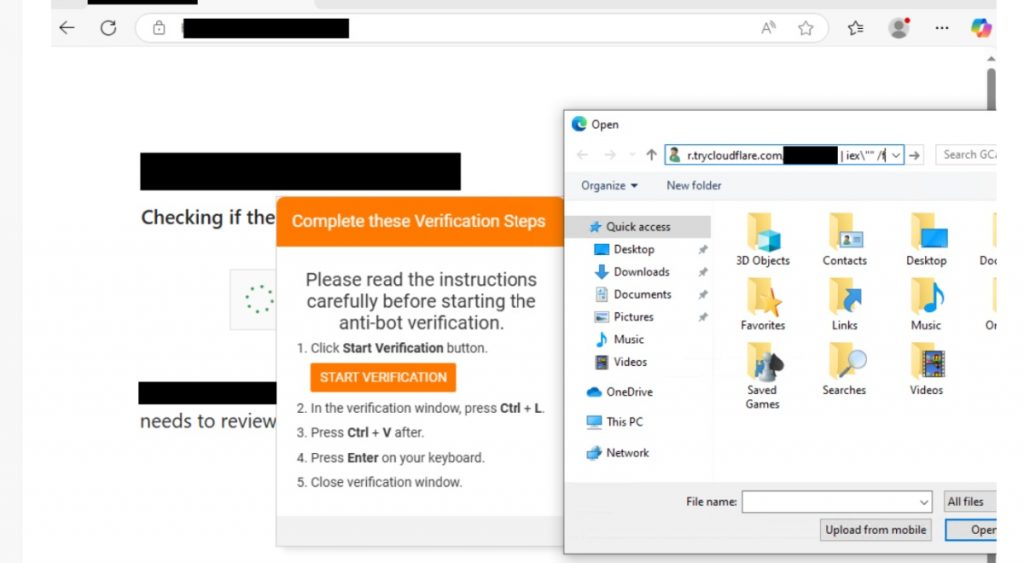
Source: The DFIR Report and Proofpoint.
From RATs to Ransom: Credential Harvesting, CobaltStrike, and Infostealers
Once inside a network, Interlock operators waste little time. Security researchers have observed the use of both RATs and CobaltStrike tools to establish a remote command and control (C2) infrastructure. PowerShell scripts are typically used to deploy credential-harvesting malware, such as LumanStealer, along with keyloggers. This enables lateral movement, privilege escalation, and data exfiltration.
The group’s ransomware encryptors are developed for both Windows and Linux systems. They commonly leverage remote desktop tools like AnyDesk to transfer malicious payloads and encrypted data.
Encryption is followed by appending file extensions such as .interlock or .1nt3rlock. Victims then receive ransom notes that direct them to Interlock’s dark web site, the “Worldwide Secrets Blog”, to negotiate payment—usually in Bitcoin.
“Your network was compromised, and we have secured your most vital files,” the group wrote to Kettering Health in May, claiming to have stolen 1 terabyte of data and threatening public release if ransom demands weren’t met.
High-Profile Targets and Global Reach
Healthcare systems appear to be a primary focus for Interlock. In May 2025, the group attacked Kettering Health, a major Midwest U.S. healthcare network. The ransomware event spanned weeks, forcing cancellation of thousands of medical procedures across 14 hospitals and over 120 outpatient clinics. Other medical institutions, including dialysis giant DaVita, have also been named among Interlock’s targets.
Interlock’s campaign is not limited to healthcare. The group has also gone after education, government, manufacturing, and tech organizations—primarily in the U.S., Canada, and parts of Europe. Their double extortion tactics involve both encryption and public threats to leak sensitive data, maximizing pressure on victims.
Nick Tausek, Lead Security Automation Architect at Swimlane, emphasized the tactical flexibility of the group:
“The group has used ClickFix attacks to impersonate IT tools and infiltrate networks, deployed remote access trojans (RATs) to deliver malware, and, most recently, adopted double extortion tactics to maximize pressure on victims.”
Possible Ties to Rhysida Ransomware Group
Security researchers have noted code similarities between Interlock ransomware variants and those used by the Rhysida threat group, a Russian-linked actor. This has led to speculation that Interlock may be a rebranded offshoot or affiliated operation.
National Cybersecurity Advisory: Harden Defenses Now
Given the group’s aggressive behavior and demonstrated ability to disrupt essential services, CISA and its federal partners urge organizations in healthcare, education, and critical infrastructure to apply rigorous cybersecurity practices. These include:
- Updating and patching software regularly
- Implementing network segmentation
- Disabling macros from email attachments
- Conducting employee phishing awareness training
- Monitoring for unusual use of remote access tools
“Interlock Ransomware serves as a stark example of how dangerous and unpredictable today’s ransomware groups have become,” said Tausek.
The group’s tactics continue to evolve, and with a growing number of successful intrusions, Interlock is quickly cementing its place as one of the most formidable ransomware threats of 2025.









