A cascading supply chain attack, originating from a compromised GitHub Action, has resulted in the exposure of CI/CD secrets affecting thousands of repositories.
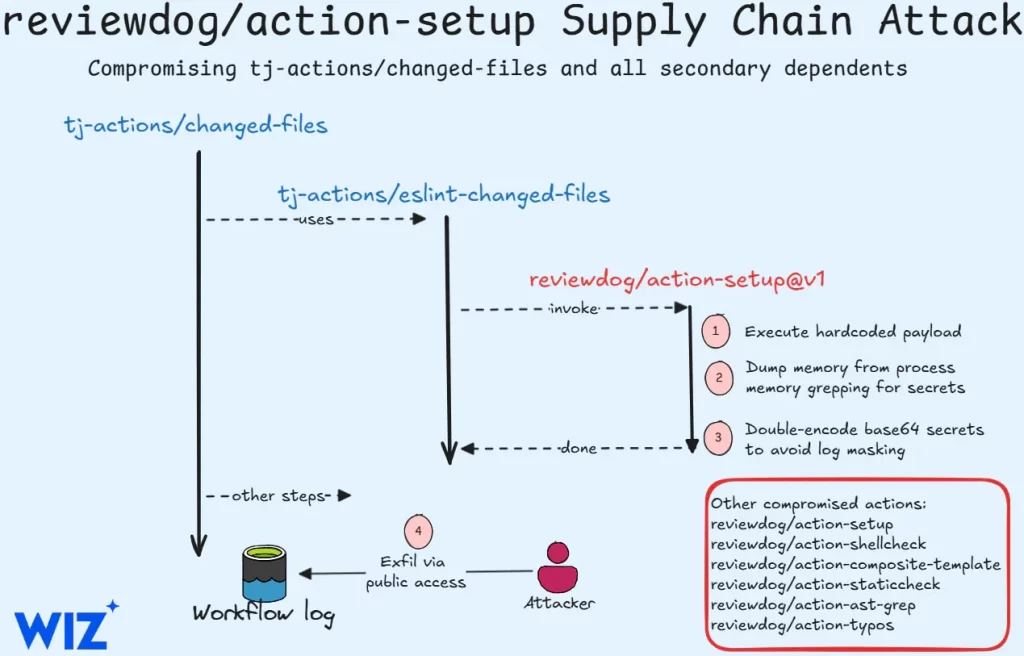
The initial compromise involved the reviewdog/action-setup@v1 GitHub Action. Attackers injected malicious code designed to extract CI/CD secrets and write them to workflow logs. This malicious code was base64-encoded and inserted into install.sh. If these logs were public, the attacker could easily steal the secrets.
GitHub Action Hack Cascaded into Another Supply Chain Attack
This attack then cascaded to the tj-actions/changed-files GitHub Action. This action, which utilizes reviewdog/action-setup, was subsequently compromised, leading to the leakage of CI/CD secrets for approximately 23,000 repositories. The tj-actions developers were unable to determine precisely how attackers compromised the GitHub Personal Access Token (PAT) used by their bot.
Wiz researchers linked the two incidents, suggesting the compromised reviewdog/action-setup action was the root cause.
“We believe that it is likely the compromise of reviewdog/action-setup is the root cause of the compromise of the tj-actions-bot PAT,”.
The researchers explain
The researchers noted that tj-actions/eslint-changed-files uses reviewdog/action-setup@v1, and the tj-actions/changed-files repository runs this action with a PAT.
The timing of both compromises further supports this theory.
The compromised reviewdog/action-setup@v1 tag allowed attackers to inject the malicious payload, exposing secrets from affected CI workflows. These secrets would have been visible in public repository workflow logs.
Supply chain attack overview
Source: Wiz
Beyond reviewdog/action-setup@v1, other actions by the same developer may also be affected, including:
reviewdog/action-shellcheckreviewdog/action-composite-templatereviewdog/action-staticcheckreviewdog/action-ast-grepreviewdog/action-typos
Wiz researchers reported their findings to the reviewdog team and GitHub. While the exact breach method remains undetermined, Wiz noted that reviewdog‘s large contributor base and automated invite system increase the risk of such compromises. The researchers warned that if the action remained compromised, a repeat attack on tj-actions/changed-files could easily succeed, potentially exposing newly rotated CI/CD secrets.
GitHub Action Hack Mitigation
To mitigate the risk, Wiz recommends the following actions:
- Run this GitHub query to check for references to
reviewdog/action-setup@v1. - Look for double-encoded base64 payloads in workflow logs as an indicator of leaked secrets.
- Immediately remove references to affected actions, delete workflow logs, and rotate potentially compromised secrets.
- Pin GitHub Actions to commit hashes instead of version tags.
- Utilize GitHub’s allow-listing feature to restrict unauthorized actions.
Helpful Reads: