According to Barracuda, a leading network and email security firm, they have successfully applied remote patches to all active Barracuda Email Security Gateway (ESG) appliances on December 21 to contain the latest Barracuda zero day exploit.
These patches were specifically designed to address a Barracuda zero day vulnerability that was being exploited by UNC4841 Chinese hackers.
Additionally, Barracuda also released a secondary wave of security updates on December 22 for Barracuda secure email gateway appliances that had already been compromised. This update was crucial in neutralizing the SeaSpy and Saltwater malware that had been deployed by the attackers.
The Barracuda Zero Day Vulnerability Lies in Amavis Virus Scanner
On Christmas Eve, the Barracuda zero day vulnerability in the Barracuda ESG appliances was revealed and assigned the CVE-2023-7102 identifier.
This vulnerability stems from a weakness found in the Spreadsheet::ParseExcel third-party library, which is utilized by the Amavis virus scanner on Barracuda ESG appliances. Exploiting this flaw allows attackers to execute unauthorized code on unpatched Barracuda email security gateway appliances by means of parameter injection.
Barracuda has taken the necessary steps and filed the CVE-2023-7101 CVE ID to track this Barracuda zero day bug separately in the open-source library. However, a patch for this vulnerability is still pending.
“No action is required by customers at this time, and our investigation is ongoing,” Barracuda says in the advisory issued on December 24.
“Barracuda, working in collaboration with Mandiant, assesses this activity is attributable to continued operations of the China nexus actor tracked as UNC4841.”
“For organizations utilizing Spreadsheet::ParseExcel in their own products or services, we recommend reviewing CVE-2023-7101 and promptly taking necessary remediation measures.”
CVE-2023-7102 Amongst the Chain of Successive Barracuda Zero Day Attacks
In a previous incident, the same group of hackers targeted Barracuda email protection by exploiting Barracuda ESG appliances using a different zero-day vulnerability known as CVE-2023-2868. This attack was part of a larger cyber-espionage campaign.
Barracuda recently disclosed that this particular zero-day exploit was being used by attackers for a period of at least seven months, starting from October 2022. The attackers leveraged this Barracuda zero day vulnerability to deploy previously unidentified malware and extract sensitive data from compromised systems.
To gain unauthorized access to compromised systems, the hackers utilized the SeaSpy and Saltwater malware, along with the SeaSide malicious tool, which enabled them to establish remote connections through reverse shells.
Additionally, they deployed Submarine (also known as DepthCharge) and Whirlpool malware as later-stage payloads. These malicious tools were used to maintain persistence on a limited number of previously compromised devices within high-value target networks.
The UNC4841 hackers were primarily driven primarily by espionage, specifically targeting high-profile government and high-tech users. According to cybersecurity firm Mandiant, nearly one-third of the compromised appliances during the May campaign belonged to government agencies. This was particularly prominent between October and December 2022.
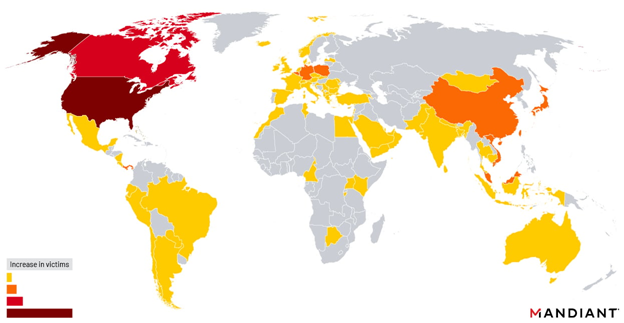
Map of Barracuda customers affected by May attacks
In response to the attacks, Barracuda issued a warning to its customers, urging them to replace all compromised Barracuda email protection appliances immediately, even if they had already applied patches.
It was discovered that approximately 5% of all appliances had been breached during the attacks.