A newly uncovered cyber espionage campaign by Chinese state-sponsored group APT41 has revealed the group’s use of Google Calendar as a command-and-control (C2) platform to manage malware and exfiltrate data. The attack, discovered by Google’s Threat Intelligence Group (GTIG), marks an unprecedented abuse of a widely used productivity tool for covert cyber operations.
Malware Communication via Calendar Events in Targeted Espionage Campaign
In October 2024, GTIG uncovered an attack where APT41 deployed malware hosted on a compromised government website. The infection began with spear phishing emails containing links to a malicious ZIP archive. This archive held a shortcut (.lnk) file disguised as a PDF and a folder of images, two of which were weaponized to deploy malware.
The malware, dubbed TOUGHPROGRESS, operates on Windows systems and interacts with Google Calendar to execute commands and extract stolen data. It creates specific calendar events to:
- Send encrypted commands to infected systems
- Exfiltrate collected data via event descriptions
- Blend malicious activity with legitimate Calendar usage
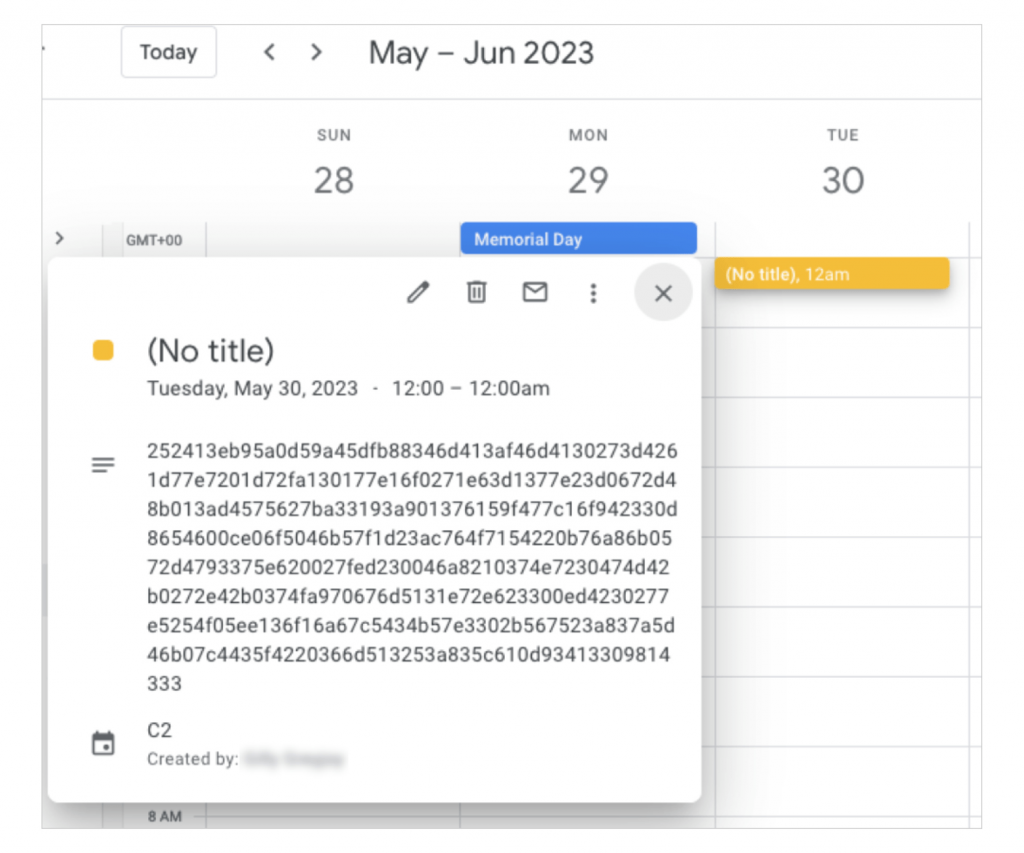
“Once executed, TOUGHPROGRESS creates a zero-minute Calendar event at a hardcoded date, 2023-05-30, with data collected from the compromised host being encrypted and written in the Calendar event description,” Google stated.
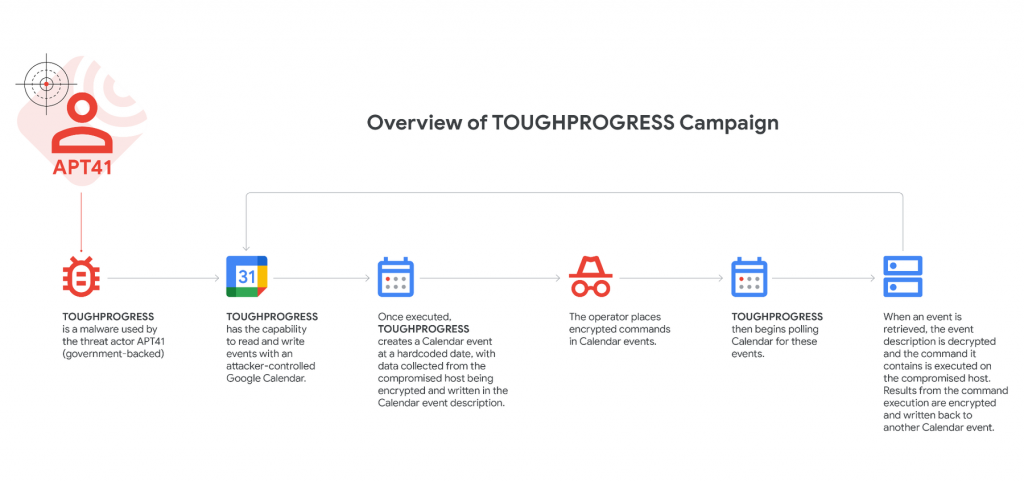
The malware checks Calendar at preset intervals, decrypts command instructions from event fields, and performs the requested actions—allowing covert remote control without triggering traditional security alerts.
Previous Cases of Google Platform Abuse by APT41
This is not the first time APT41 has misused Google’s services for cyber operations. In April 2023, the group used Google Sheets to manage malware and Google Drive for data exfiltration. It also misused Google AMP cache URLs to redirect users to malicious, password-protected 7-Zip archives hosted on third-party services like OpenDrive.
GTIG emphasized that this campaign reflects a broader trend:
“APT continues to use free web hosting tools for malware distribution, sending malicious links to hundreds of targets across the globe.”
Google Dismantles APT41’s Calendar-Based C2 Infrastructure
Upon identifying the campaign, Google acted to neutralize the infrastructure. The company:
- Developed custom fingerprints to detect malicious Calendar use
- Terminated attacker-controlled Workspace projects
- Updated file detections
- Added domains and URLs to the Safe Browsing blocklist
- Notified affected organizations and assisted in mitigation
“We have developed custom fingerprints to identify and take down attacker-controlled Calendars,” GTIG said.
“We have also terminated attacker-controlled Workspace projects, effectively dismantling the infrastructure that APT41 relied on for this campaign.”
The targeting in this campaign focused on government entities, but APT41’s known history includes espionage against the logistics, media, entertainment, technology, and automotive sectors.