A New Breed of Malware Emerges, Targeting Businesses Worldwide
A new malware campaign has emerged, targeting organizations across the globe with a previously undocumented backdoor named “Voldemort.” This campaign, which began on August 5, 2024, has already disseminated over 20,000 emails to over 70 targeted organizations, reaching a peak of 6,000 emails in a single day. The threat actor behind this campaign remains unidentified, but security researchers at Proofpoint believe the primary objective is cyber espionage.
The Campaign’s Tactics: A Multi-Stage Attack
The Voldemort campaign employs a sophisticated multi-stage attack, leveraging social engineering, phishing techniques, and a unique approach to command and control (C2) infrastructure. Here’s a breakdown of the attack stages:
1. Impersonating Tax Authorities:
The attackers craft phishing emails that mimic the appearance of legitimate communications from tax agencies in the targeted organization’s country. These emails often contain subject lines referencing updated tax information and include links to associated documents.
2. Deceptive Landing Pages:
Clicking on the provided link directs victims to a landing page hosted on InfinityFree, which utilizes Google AMP Cache URLs to redirect them to a page with a “Click to view document” button.
3. Exploiting Windows Search Protocol:
When the button is clicked, the page checks the browser’s User Agent. If it detects a Windows device, the victim is redirected to a search-ms URI (Windows Search Protocol) that points to a TryCloudflare-tunneled URI. This technique makes the malicious file appear as if it resides locally in the Downloads folder, tricking victims into opening it.
4. Python Script Execution and Decoy PDF:
Opening the search-ms file executes a Python script from a remote WebDAV share without downloading it to the host. This script performs system info collection to profile the victim and simultaneously displays a decoy PDF to distract from the malicious activity.
5. DLL Side-Loading and Voldemort Deployment:
The script downloads a legitimate Cisco WebEx executable (CiscoCollabHost.exe) and a malicious DLL (CiscoSparkLauncher.dll). Voldemort is then loaded into the system using DLL side-loading.
Voldemort: A Powerful Backdoor with Unique C2 Capabilities
Voldemort is a C-based backdoor that provides attackers with a wide range of capabilities, including:
- Data Exfiltration: Stealing sensitive data from infected systems.
- Payload Delivery: Introducing new payloads into the system for further malicious activity.
- File Management: Deleting files and manipulating directories on the infected system.
Google Sheets: An Unexpected Command and Control Center
A notable feature of Voldemort is its use of Google Sheets as a command and control server (C2). The malware pings the Google Sheet to receive new commands to execute on the infected device and uses it as a repository for stolen data.
Data Storage and Organization:
Each infected machine writes its data to specific cells within the Google Sheet, which can be designated by unique identifiers like UUIDs. This ensures isolation and facilitates clear management of the compromised systems.
Reliable and Highly Available C2:
Voldemort utilizes Google’s API with an embedded client ID, secret, and refresh token to interact with Google Sheets. This approach provides a reliable and highly available C2 channel, reducing the likelihood of network communication being flagged by security tools.
Leveraging a Common Enterprise Tool:
Google Sheets is widely used in enterprise environments, making blocking the service impractical.
Defending Against the Voldemort Threat
To mitigate the risk of falling victim to the Voldemort campaign, Proofpoint recommends the following security measures:
- Limit Access to External File-Sharing Services: Restrict access to external file-sharing services to trusted servers only.
- Block Connections to TryCloudflare: Block connections to TryCloudflare unless actively needed.
- Monitor for Suspicious PowerShell Execution: Monitor for suspicious PowerShell execution, as this is often used by attackers to deploy malware.
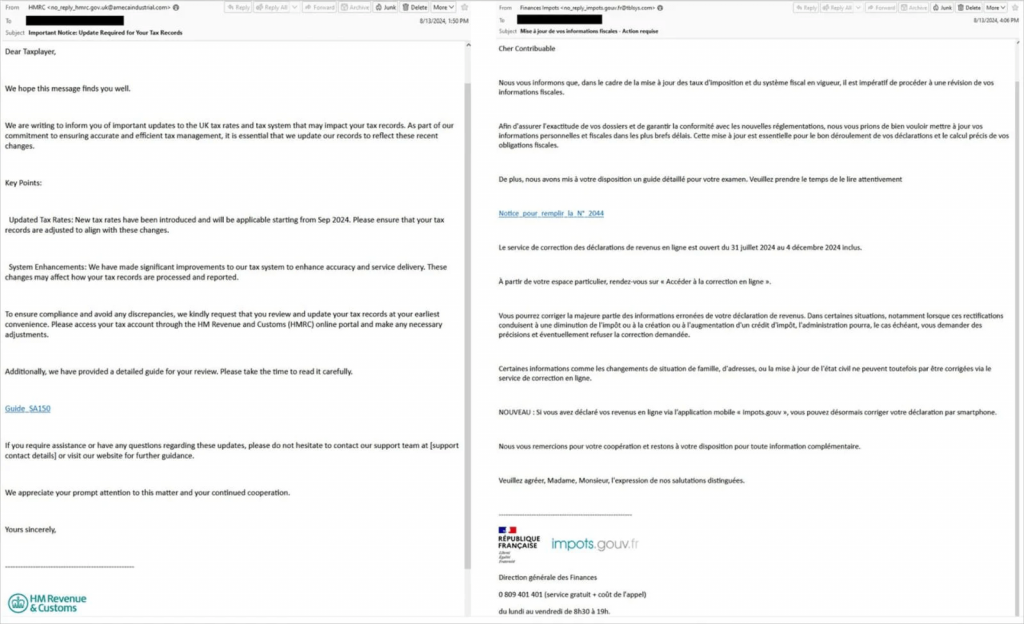
Samples of the malicious emails used in the campaign
Source: Proofpoint
The Importance of Proactive Security Measures
The Voldemort campaign demonstrates the ever-evolving nature of cyberattacks. Attackers are constantly seeking new ways to exploit vulnerabilities and bypass security defenses. Enterprise businesses must adopt a proactive security posture to protect themselves from these threats.
Key Takeaways for Enterprise Businesses:
- Prioritize Security Awareness: Educate employees about phishing attacks and the importance of verifying communications before clicking on links or opening attachments.
- Implement Strong Password Policies: Enforce strong password policies and encourage the use of multi-factor authentication.
- Utilize Threat Intelligence: Stay informed about emerging threats and vulnerabilities. Leverage threat intelligence feeds to identify potential attacks and take appropriate security measures.
- Regularly Patch Systems: Keep all software and operating systems up to date with the latest security patches.
- Monitor Network Activity: Implement network monitoring tools to detect suspicious activity and identify potential intrusions.
- Conduct Security Audits: Regularly conduct security audits to identify vulnerabilities and weaknesses.
By taking these steps, enterprise businesses can significantly reduce their risk of falling victim to sophisticated cyberattacks like the Voldemort campaign. Remember, proactive security is essential for protecting your business from the ever-growing threat of ransomware and other cyber threats.









