A hacking group known as ‘UAC-0184’ using steganographic image files and IDAT loader Malware to distribute the Remcos RAT (remote access Trojan) on the systems of a Ukrainian entity operating in Finland.
UAC-0184 has previously targeted the Armed Forces of Ukraine using the same malware. Recent activity by this threat group, detected by analysts at Morphisec, indicates that they have expanded their targets to include organizations outside of Ukraine that are connected to their strategic objective.
While specific details about the victim cannot be shared due to confidentiality, Morphisec has provided some information on the attack methods used.
Using Steganography for Loading IDAT Loader and Remcos RAT Malware
Steganography is a known strategy that involves hiding malicious code within image pixels to avoid detection by security systems that rely on signature-based rules. Usually, the code is embedded in a way that doesn’t visibly alter the image.
However, in the case observed by Morphisec, the image does appear distorted. It’s important to note that this distortion would only pose a risk to attackers if the image was manually inspected. Otherwise, it effectively evades detection from automated security products.
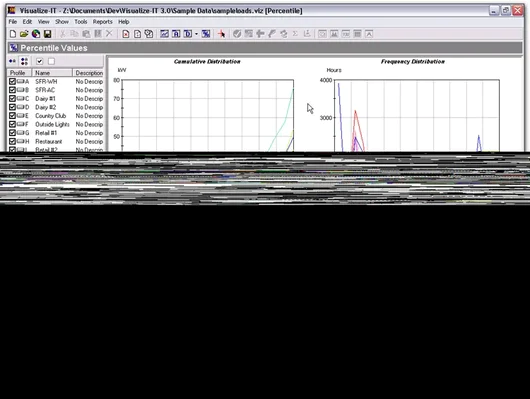
Malicious PNG image containing embedded code
Source: (Morphisec)
The attack sequence observed by Morphisec begins with a sophisticated phishing email purporting to be from either Ukraine’s 3rd Separate Assault Brigade or the Israel Defense Forces. Unsuspecting recipients who open the attached shortcut file unknowingly initiate a series of infections. This chain of events leads to the execution of an executable file called DockerSystem_Gzv3.exe, which then activates a modular malware loader known as ‘IDAT.’
“Distinguished by its modular architecture, IDAT employs unique features like code injection and execution modules, setting it apart from conventional loaders,” “It employs sophisticated techniques such as dynamic loading of Windows API functions, HTTP connectivity tests, process blocklists, and syscalls to evade detection.” describes Morphisec.
To maintain stealth, the API calls in the code are not directly written in plain text. Instead, they are resolved dynamically during runtime using a decryption key that is part of the attack chain.
The IDAT Loader Module Loads the
The IDAT loader module is responsible for extracting the encoded payload from the malicious PNG image file. It then decrypts and executes the payload in the computer’s memory. This process involves multiple stages and includes injecting additional modules into legitimate processes like Explorer.exe and DLL files like PLA.dll.
In the final stage, the encrypted Remcos remote access Trojan is decrypted and executed. This remote access Trojan is a commonly used malware that hackers employ as a backdoor on compromised systems. It allows for covert data theft and monitoring of the victim’s activities.
According to Morphisec, the IDAT loader module is also responsible for delivering malware such as Danabot, SystemBC, and RedLine Stealer. However, it is unclear whether these specific families were observed in the Finnish-based computers or in separate attacks.
For the complete list of indicators of compromise (IoC) associated with this campaign, it is recommend referring to the report by CERT-UA. They provide detailed information on the IoCs related to this particular attack.