Security researchers have discovered that more than 178k SonicWall firewalls are vulnerable to DOS and RCE attacks. This flaw was found in vulnerable SonicWall firewalls with exposed online management interfaces. These vulnerable SonicWall firewalls are susceptible to denial-of-service (DoS) and potential remote code execution (RCE) attacks.
178K SonicWall Firewalls Allow Remote Code Execution
Almost 180k Internet-Exposed SonicWall Firewalls are concerning as one of the flaws allows Remote Code Execution.
These vulnerable SonicWall appliances are affected by two Sonicwall DoS security flaws known as CVE-2022-22274 and CVE-2023-0656, with the former also enabling attackers to achieve remote code execution.
“Using BinaryEdge source data, we scanned SonicWall firewalls with management interfaces exposed to the internet and found that 76% (178,637 of 233,984) are vulnerable to one or both issues,”
Jon Williams, a Senior Security Engineer at Bishop Fox.
According to the findings of Bishop Fox, the two vulnerabilities, although stemming from the same vulnerable code pattern, can be exploited at different HTTP URI paths. This discovery highlights the extensive attack surface of these vulnerabilities.
“Our initial research confirmed the vendor’s assertion that no exploit was available; however, once we identified the vulnerable code, we discovered it was the same issue announced a year later as CVE-2023-0656,”
“We found that CVE-2022-22274 was caused by the same vulnerable code pattern in a different place, and the exploit worked against three additional URI paths.”
In addition to the potential for remote code execution, these vulnerabilities can also be exploited by attackers to force targeted appliances into maintenance mode.
This would then require administrators to intervene and restore normal functionality. Consequently, even without confirming the possibility of remote code execution, malicious actors can utilize these vulnerabilities to disable edge firewalls and compromise VPN access to corporate networks.
Data from the threat monitoring platform Shadowserver reveals that there are currently more than 500,000 vulnerable SonicWall firewalls exposed online, with a significant portion of them, over 328,000, located in the United States.
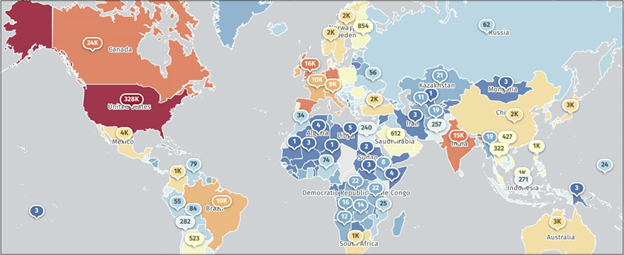
Internet-exposed SonicWall firewalls (ShadowServer)
While the SonicWall Product Security Incident Response Team (PSIRT) has not received any reports of these vulnerabilities being exploited in real-world scenarios, it is crucial to acknowledge that there is at least one proof-of-concept (PoC) exploit for CVE-2022-22274 accessible online.
This situation underscores the potential risk linked to these vulnerabilities and emphasizes the importance of promptly implementing mitigation measures.
Vulnerable SonicWall Firewalls Can Assist Hackers in Cyber Espionage Campaigns
An example of the potential consequences of these vulnerabilities can be seen in a previous incident. Last March, SonicWall PSIRT and Mandiant disclosed that suspected Chinese hackers had implanted customized malware on unpatched SonicWall Secure Mobile Access (SMA) appliances.
This allowed them to maintain long-term persistence in cyber-espionage campaigns. In another instance, customers were urgently advised in July to patch critical authentication bypass flaws in SonicWall’s GMS firewall management and Analytics network reporting products.
It is important to note that SonicWall serves a substantial customer base, with over 500,000 businesses across more than 215 countries and territories.
This includes government agencies and some of the largest companies globally. This underscores the significance of addressing these vulnerabilities promptly and effectively.









