A recently discovered Linux variant of the Bifrost malware RAT (remote access Trojan) has implemented several innovative methods to evade detection.
This includes the use of a deceptive domain that mimics VMware. Bifrost has been a persistent threat for two decades, typically infecting users through malicious email attachments or payload-dropping sites to gather sensitive information.
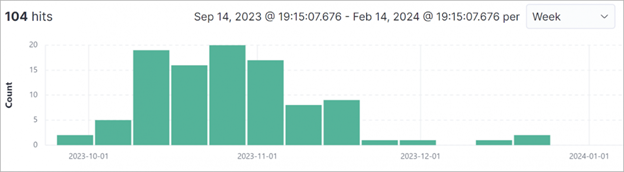
Researchers from Palo Alto Networks’ Unit 42 have noticed a recent surge in Bifrost’s activity, prompting them to conduct an investigation that uncovered an updated and more covert variant.
Source: (Unit 42)
Bifrost Malware Tactics
Through their analysis of the latest Bifrost Malware samples, researchers from Unit 42 have discovered significant enhancements that improve the malware’s functionality and ability to avoid detection.
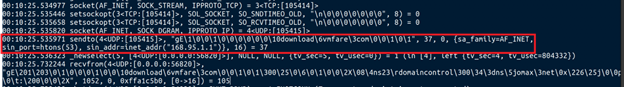
One notable update is the use of a command and control (C2) server with the domain “download.vmfare[.]com,” cleverly designed to resemble a legitimate VMware domain.
This deceptive tactic increases the chances of the malware going unnoticed during inspection. Additionally, the malware leverages a public DNS resolver based in Taiwan to resolve the deceptive domain, making it more challenging to trace and block.
Source: (Unit 42)
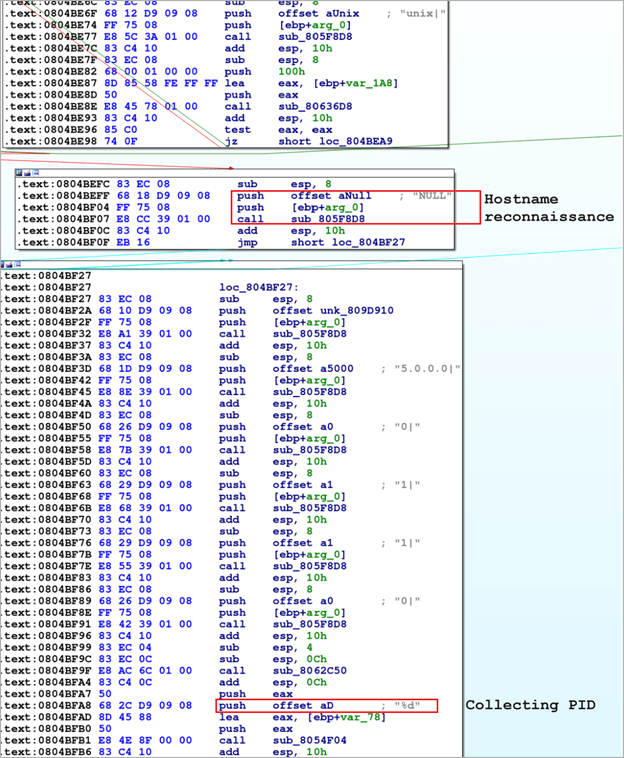
From a technical standpoint, the Bifrost malware presents challenges for analysis as its binary is compiled without debugging information or symbol tables, making it more difficult to dissect.
Once infected, Bifrost gathers the victim’s hostname, IP address, and process IDs, encrypting this data using the RC4 encryption algorithm before transmitting it to the command and control (C2) server through a newly established TCP socket.
Source: (Unit 42)
Additionally, Unit 42’s report highlights the discovery of an ARM version of Bifrost Malware, which exhibits the same functionality as the x86 samples examined in their analysis.
The introduction of these builds indicates that the attackers are expanding their focus to ARM-based architectures, which are growing in popularity across different environments.
While Bifrost Malware may not be considered a highly advanced or widely distributed malware, the findings from the Unit 42 team emphasize the need for heightened vigilance. The RAT’s developers are evidently working towards enhancing its stealth capabilities and expanding its ability to target a broader range of system architectures.