The Bigpanzi cybercrime gang has been generating substantial profits by infecting Android TV, Android TV boxes and various eCos set-top boxes with Bigpanzi botnet malware, globally since at least 2015.
According to Beijing-based Qianxin Xlabs, the Bigpanzi cybercrime group operates a vast botnet consisting of approximately 170,000 active bots on a daily basis. However, since August, researchers have observed 1.3 million unique IP addresses associated with the Bigpanzi botnet, with the majority located in Brazil.
Bigpanzi gains access to these devices by exploiting firmware updates or by tricking users into installing compromised applications themselves. This information was highlighted in a report by Dr. Web in September 2023.
The perpetrators capitalize on these infections by transforming the compromised set top boxes into nodes for illicit media streaming platforms, traffic proxy networks, distributed denial of service (DDoS) swarms, and over-the-top (OTT) content provision.
Malicious software with malware payloads
Source: Xlabs
Bigpanzi’s Custom Malware Uses ‘Pandoraspear’ and ‘Pcdn’ to Hijack DNS and Establish C2 COMs
The report from Xlabs primarily examines two malware tools employed by Bigpanzi, namely ‘pandoraspear’ and ‘pcdn’.
Pandoraspear operates as a backdoor trojan, enabling the hijacking of DNS settings, establishing communication with a command and control (C2) server, and executing commands received from the C2 server.
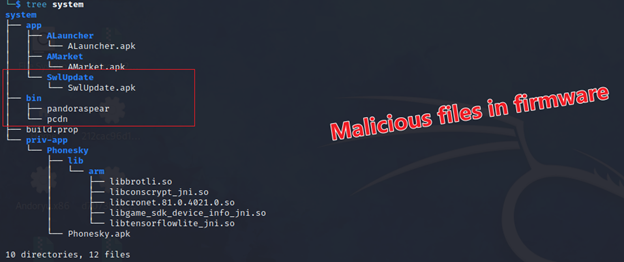
‘Pandoraspear’ and malware payloads
Source: Xlabs
This malicious software possesses a range of capabilities, including the manipulation of DNS settings, initiation of distributed denial of service (DDoS) attacks, self-updating functionality, establishing communication with the C2 server, creation of reverse shells, and execution of arbitrary operating system (OS) commands.
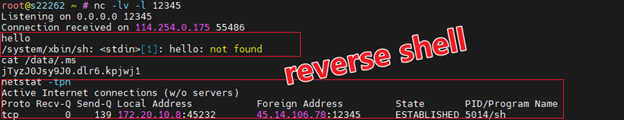
Malware creating a reverse-shell on the infected device
Source: Xlabs
The functionality of pandoraspear allow Bigpanzi to effectively control the compromised devices, carry out their malicious activities, and evade detection.
Pandoraspear employs advanced techniques, such as modified UPX shell, OLLVM compilation, dynamic linking, and anti-debugging mechanisms, to cleverly evade detection by security measures.
On the other hand, pcdn serves the purpose of establishing a peer-to-peer (P2P) Content Distribution Network (CDN) on compromised devices.
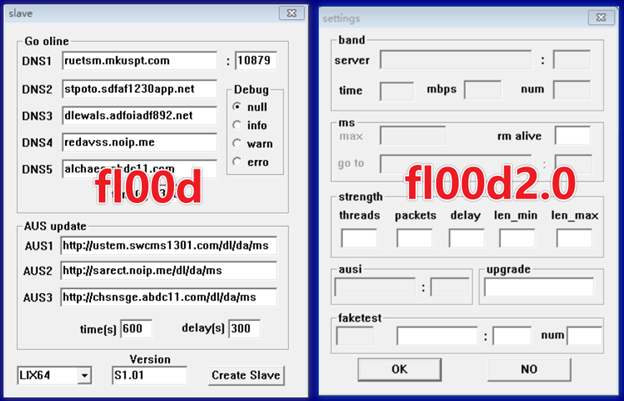
Pcdn’s ‘Fl00d’ DDoS toolset
Source: Xlabs
Additionally, it possesses capabilities for launching DDoS attacks, effectively turning these devices into weapons.
Bigpanzi Botnet Boasts a Large Scale of operations with 170,000 Active Bots
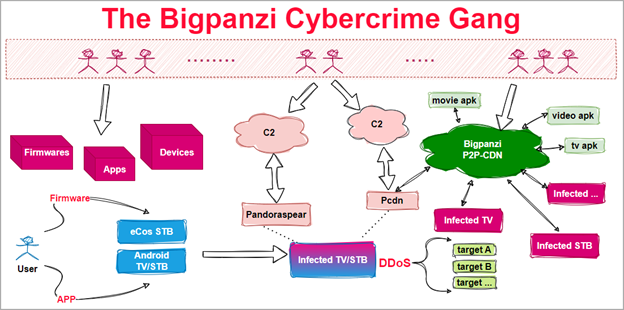
Bigpanzi Modus Operandi
Source: Xlabs
Xlabs obtained valuable information regarding the extent of the botnet by intercepting and taking control of two command and control (C2) domains utilized by the attackers.
Through a seven-day observation period, the analysts concluded that the Bigpanzi botnet reaches its peak with approximately 170,000 active bots on a daily basis. Moreover, since August, they have identified over 1.3 million unique IP addresses associated with the botnet.
However, it is important to note that the actual size of the botnet is likely larger. This is due to the fact that not all compromised Smart TV boxes are active simultaneously, and the visibility of the cybersecurity analysts is limited, preventing them from capturing the complete scope of the botnet’s scale.
“Over the past eight years, Bigpanzi has been operating covertly, silently amassing wealth from the shadows,”
“With the progression of their operations, there has been a significant proliferation of samples, domain names, and IP addresses.”
“In the face of such a large and intricate network, our findings represent just the tip of the iceberg in terms of what Bigpanzi encompasses.”
Reads the Xlabs report.
Based on their analysis of the pcdn sample, researchers have discovered artifacts that have led them to a suspicious YouTube channel, which they suspect is controlled by a specific company. However, the Xlabs report has not provided any specific attribution details at this time.
It is likely that they are withholding this information, reserving it for the relevant law enforcement authorities who are responsible for investigating and taking appropriate action against the cybercriminals associated with the Bigpanzi cyber crime gang.









