A stealthy cyber-espionage campaign is underway targeting Russian industrial companies with a previously undocumented Windows spyware called Batavia. The malware is distributed through phishing emails disguised as contract documents. According to security researchers, the operation has been running since mid-2024 and remains active.
Attack Begins with Contract-Themed Emails That Drop Malware via Scripted Archives
The campaign starts with phishing emails impersonating business correspondence, luring recipients to click on a link that appears to lead to a contract. That link downloads an archive containing a malicious .VBE script (Visual Basic Encoded file).
Once opened, the script silently profiles the infected system and sends the details to a command-and-control server hosted at oblast-ru[.]com, setting the stage for further malicious actions.
Initial Malware Tool Distracts Victims While Collecting Sensitive Files
Following the system profiling, the attacker delivers the first major spyware component, named WebView.exe. This Delphi-based executable presents a decoy contract window to make the interaction appear normal, while behind the scenes it:
- Captures screenshots
- Collects system logs and documents
- Sends stolen data to a remote server at
ru-exchange[.]com
To avoid uploading duplicates, the malware calculates a hash of the first 40,000 bytes of each file and skips any already sent.
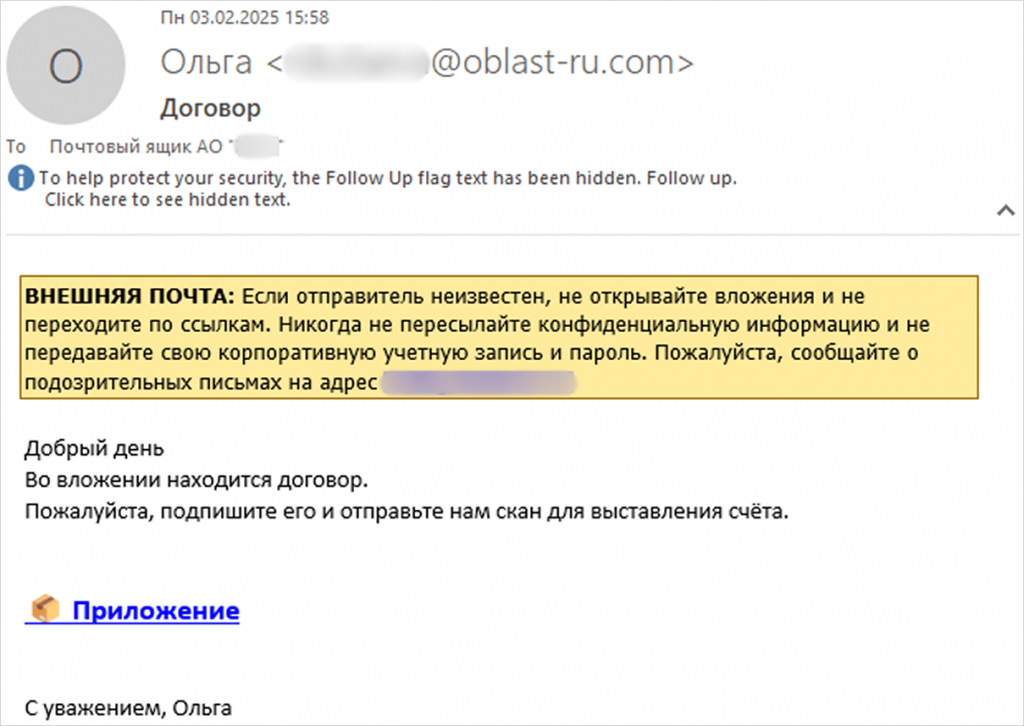
Email used in the Batavia campaign
Source: Kaspersky
Follow-Up Tool Increases Data Theft and Ensures Malware Persistence
Once data collection is underway, another payload called javav.exe is delivered to the infected machine. This C++ component is more invasive. It:
- Adds a shortcut to run at every system startup
- Expands the file search to include emails, images, spreadsheets, archives, RTFs, TXTs, and presentations
This ensures that a broader range of sensitive data is harvested over time.
Unconfirmed Malware Component May Play a Role in Further Exploitation
Researchers suspect there is yet another component named windowsmsg.exe, which was referenced in the malware logic but not successfully retrieved. Its function remains unknown but is likely linked to additional exploitation or data theft capabilities.
Evidence Suggests Industrial Espionage Behind the Campaign
Telemetry from Kaspersky indicates that the campaign began as early as July 2024, with attacks intensifying into early 2025. Emails carrying Batavia spyware have reached employees across dozens of industrial enterprises in Russia.
While attribution has not been confirmed, the type of targets and the malware’s focus on internal documents, screenshots, and emails strongly indicate a covert surveillance operation aimed at understanding or disrupting Russia’s industrial activity.









