The Vo1d botnet has recently reached alarming heights, infecting over 1.59 million Android TV devices globally, impacting 226 countries. This significant surge in infections highlights the evolving nature of malware targeting consumer electronics.
Details on Infection and Spread Vo1d Botnet
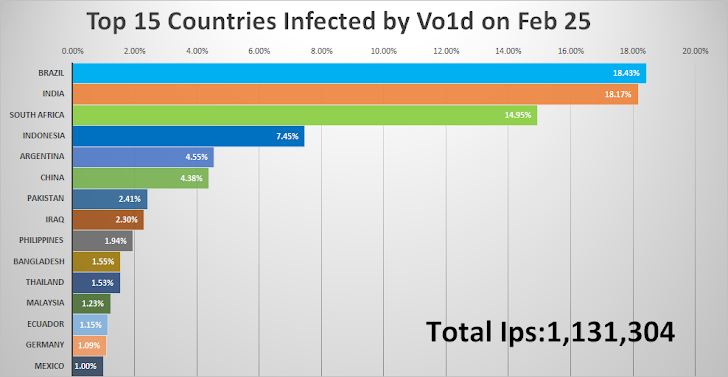
As of January 19, 2025, the Vo1d botnet peaked at 1,590,299 infected devices. The botnet operates using 800,000 daily active IP addresses. Notably, India has seen a dramatic rise in infection rates, jumping from less than 1% to 18.17%, translating to 217,771 infected devices.
Technical Insights into Vo1d Botnet
According to QiAnXin XLab, the Vo1d botnet has enhanced its stealth and resilience mechanisms. The malware utilizes RSA encryption for secure network communication, making it difficult for researchers to take control. Each payload employs a unique downloader, utilizing XXTEA encryption and RSA-protected keys to complicate analysis.
“Vo1d has evolved to enhance its stealth, resilience, and anti-detection capabilities,” QiAnXin XLab stated.
Vo1d’s Method of Compromise
The precise mechanism of infection remains unclear. However, it is suspected that attackers may be leveraging supply chain attacks or targeting devices running unofficial firmware with built-in root access. Google confirmed that the affected devices are “off-brand” models not certified by Play Protect, likely utilizing the Android Open Source Project (AOSP) code.
Vo1d Botnet Operations and Capabilities
The Vo1d botnet is geared toward creating a proxy network and engaging in advertisement click fraud. It operates under a “rental-return” model, where its infrastructure is leased to other criminal entities for a specified time. This allows for illegal operations before rejoining the larger Vo1d network.
Vo1d’s Malware Analysis
A recent examination of the ELF malware variant (s63) reveals its design is to download, decrypt, and execute a secondary payload, establishing communication with a command-and-control (C2) server. The decrypted package includes critical files necessary for its operation:
- install.sh
- cv
- vo1d
- x.apk
The main function of the Vo1d module is to set up a backdoor, facilitating communication with the C2 server and executing native libraries.
“Its core functionality remains unchanged,” XLab noted. “However, significant updates to its network communication mechanisms have been introduced.”
Malicious App Behavior
The malicious Android application masquerades under the package name “com.google.android.gms.stable” to evade detection. It ensures persistence by listening for the “BOOT_COMPLETED” event, allowing it to restart automatically after a device reboot. Additionally, it launches other components similar to the Vo1d module, establishing a chain of malware activity.
Additional Malware Integration
The attack chain further leads to the deployment of a modular Android malware named Mzmess, which comprises four plugins for various illicit activities, including:
- Popa for proxy services
- Jaguar for proxy services
- Lxhwdg with an unknown purpose
- Spirit for ad promotion and traffic inflation
The distinct absence of infrastructural overlaps between Mzmess and Vo1d suggests that the operators may be renting their services to other groups for profit.
Conclusion
The Vo1d botnet is not just a profit-generating tool; its control over devices presents potential for large-scale cyber attacks, including distributed denial-of-service (DDoS) operations. As this threat evolves, organizations must remain vigilant against these sophisticated attacks.










