North Korean hackers have recently been utilizing the updating mechanism of eScan antivirus software to infiltrate large corporate networks. They achieve this by deploying GuptiMiner malware, which serves as a backdoor and delivers cryptocurrency miners.
Experts have characterized GuptiMiner as an extremely advanced threat due to its ability to execute DNS requests, extract payloads from images, digitally sign its payloads, and engage in DLL sideloading.
Delivering GuptiMiner Malware Using eScan Updates
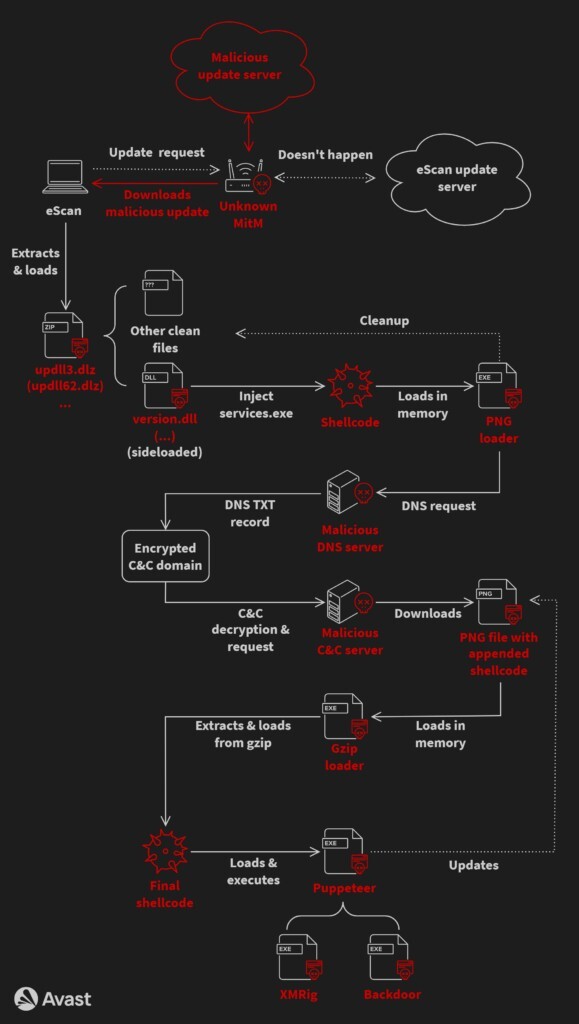
According to a report published today by cybersecurity firm Avast, the actor responsible for GuptiMiner employed an adversary-in-the-middle (AitM) technique to intercept the legitimate virus definition update package and substitute it with a malicious one called ‘updll62.dlz.’
This malicious package contained both the required antivirus updates and the GuptiMiner malware disguised as a DLL file named ‘version.dll.’ The eScan updater processed the package without suspicion, unpacking and executing it.
It is during this stage that the malware’s DLL file was surreptitiously loaded by eScan’s authorized binaries, granting the malware elevated system privileges.
Furthermore, the DLL component of GuptiMiner is designed to retrieve additional payloads from the attacker’s infrastructure.
It establishes persistence on the compromised host by creating scheduled tasks, manipulates DNS settings, injects malicious code into legitimate processes, employs code virtualization techniques, encrypts payloads using XOR encryption, and stores them in the Windows registry.
Additionally, GuptiMiner has the capability to extract executable files from PNG images.
To avoid detection in sandbox environments, GuptiMiner also conducts checks to determine if the system it is running on has more than 4 CPU cores and 4GB of RAM.
Furthermore, it actively looks for the presence of Wireshark, WinDbg, TCPView, 360 Total Security, Huorong Internet Security, Process Explorer, Process Monitor, and OllyDbg, which are commonly used monitoring and analysis tools.
In addition, AhnLab and Cisco Talos products are deactivated if they are running on the compromised machine. The diagram below illustrates the complete chain of infection:
According to Avast researchers, there are indications that GuptiMiner may be associated with the North Korean APT group Kimsuki. This inference is based on similarities between GuptiMiner’s information-stealing capabilities and the Kimsuky keylogger.
One such similarity is the utilization of the domain mygamesonline[.]org, which is typically associated with Kimsuky operations.
Malware Tools Deployed by GuptiMiner
The hackers effectively utilized GuptiMiner to distribute multiple types of malware on compromised systems. This included deploying two different backdoors as well as the XMRig Monero miner.
The first backdoor is an advanced variant of Putty Link, which was strategically placed on corporate systems. Its primary function is to scan the local network for susceptible systems and potential entry points to facilitate lateral movement.
It specifically targets Windows 7 and Windows Server 2008 systems, exploiting them through the use of SMB traffic tunneling.
Another notable component employed by the hackers is a sophisticated modular malware that conducts thorough scans on the host to locate stored private keys and cryptocurrency wallets.
To prevent repetitive scans that could attract attention, the malware creates a registry key to mark the completion of the scan.
Moreover, it has the ability to receive commands that allow for the installation of additional modules into the registry, thereby enhancing its capabilities within the compromised environment. Unfortunately, Avast did not provide further details on these additional modules.
Interestingly, the attackers also included the XMRig miner in many instances. This miner, however, stands in contrast to the overall sophistication observed in the analyzed campaign. Its inclusion may be an intentional tactic employed by the hackers to divert attention away from their primary attack strategy.
eScan’s Says They Have Addressed the Issue
Upon discovering the vulnerability exploited by the GuptiMiner campaign, Avast researchers promptly reported it to eScan, the antivirus vendor. Fortunately, eScan confirmed that they have addressed the issue and resolved the vulnerability.
In addition, eScan mentioned that the last similar report they received was in 2019. Since then, the vendor has implemented a more stringent checking mechanism to ensure that non-signed binaries are rejected, enhancing the overall security of their software.
As part of their recent implementation, eScan has also upgraded their update download process to occur over HTTPS.
This change ensures that clients interacting with the vendor’s cloud-facing servers benefit from encrypted communication, further strengthening the security measures in place.
Despite the efforts made by eScan to address the vulnerability, Avast researchers have noted that new infections by GuptiMiner are still being observed.
This may suggest that some users are running outdated versions of the eScan software, which could leave them vulnerable to attack.
To assist defenders in mitigating the threat posed by GuptiMiner, Avast has provided a comprehensive list of Indicators of Compromise (IoCs).
These IoCs can be accessed on a dedicated GitHub page, offering valuable information and resources for organizations to enhance their defenses against this particular threat.